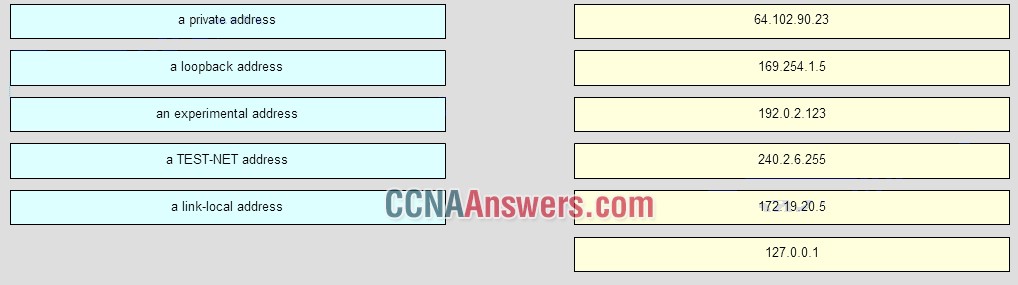
CCNA 1 Final Exam V6.0 Answers
1. Refer to the exhibit. If host A sends an IP packet to host B, what will the destination address be in the frame when it leaves host A?
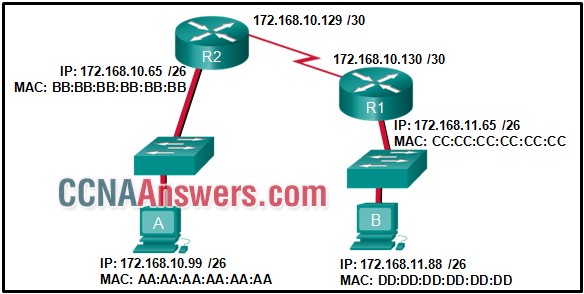
172.168.10.99
172.168.10.65
DD:DD:DD:DD:DD:DD
AA:AA:AA:AA:AA:AA
BB:BB:BB:BB:BB:BB
CC:CC:CC:CC:CC:CC
2. Which example of malicious code would be classified as a Trojan horse?
malware that was written to look like a video game
malware that requires manual user intervention to spread between systems
malware that can automatically spread from one system to another by exploiting a vulnerability in the target
malware that attaches itself to a legitimate program and spreads to other programs when launched