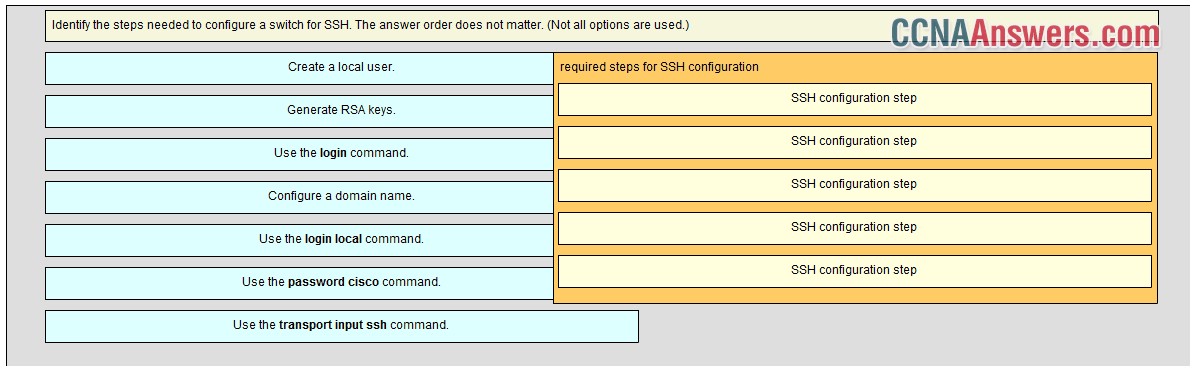
CCNA 2 Final Exam V6.0 Answers
1. Refer to the exhibit. NAT is configured on Remote and Main. The PC is sending a request to the web server. What Ipv4 address is the source IP address in the packet between Main and the web server?
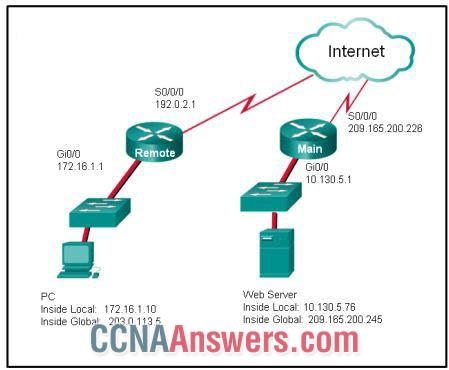
209.165.200.245
10.130.5.76
192.0.2.1
172.16.1.10
209.165.200.226
203.0.113.5
2. Which information does a switch use to populate the MAC address table?
The destination MAC address and the outgoing port
the source MAC address and the outgoing port
the destination MAC address and the incoming port
the source and destination MAC addresses and the outgoing port
the source and destination MAC addresses and the incoming port
the source MAC address and the incoming port


 ;
;