CCNA 4 Final Exam V6.0 Answers
1. Refer to the exhibit. A network administrator is troubleshooting the OSPF network. The 10.10.0.0/16 network is not showing up in the routing table of Router1. What is the probable cause of this problem?
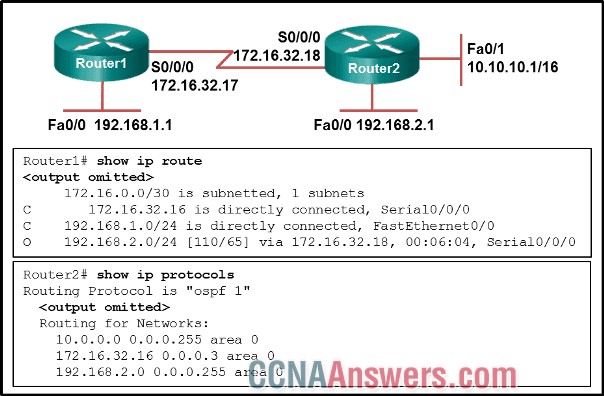
The serial interface on Router2 is down.
There is an incorrect wildcard mask statement for network 10.10.0.0/16 on Router2.
The OSPF process is configured incorrectly on Router1.
The OSPF process is not running on Router2.
2. What two protocols are supported on Cisco devices for AAA communications? (Choose two.)
RADIUS
HSRP
LLDP
VTP
TACACS+
3. Which three statements are true about PPP? (Choose three.)
PPP uses LCPs to establish, configure, and test the data-link connection.
PPP can use synchronous and asynchronous circuits.
PPP can only be used between two Cisco devices.
PPP uses LCPs to agree on format options such as authentication, compression, and error detection.
PPP carries packets from several network layer protocols in LCPs.
4. What protocol should be disabled to help mitigate VLAN attacks?
DTP
ARP
CDP
STP
5. Refer to the exhibit. Which type of Layer 2 encapsulation used for connection D requires Cisco routers?
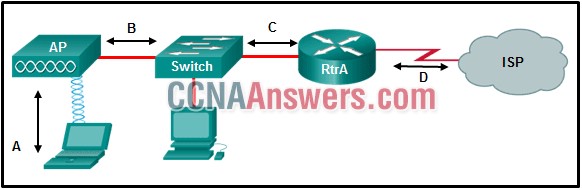
HDLC
Ethernet
PPP
PPPoE
6. What is the purpose of the generic routing encapsulation tunneling protocol?
to provide packet level encryption of IP traffic between remote sites
to manage the transportation of IP multicast and multiprotocol traffic between remote sites
to provide fixed flow-control mechanisms with IP tunneling between remote sites
to support basic unencrypted IP tunneling using multivendor routers between remote sites
7. Which troubleshooting tool would a network administrator use to check the Layer 2 header of frames that are leaving a particular host?
Knowledge base
baselining tool
CiscoView
protocol analyzer
8. Refer to the exhibit. A user turns on a PC after it is serviced and calls the help desk to report that the PC seems unable to reach the Internet. The technician asks the user to issue the arp –a and ipconfig commands. Based on the output, what are two possible causes of the problem? (Choose two.)
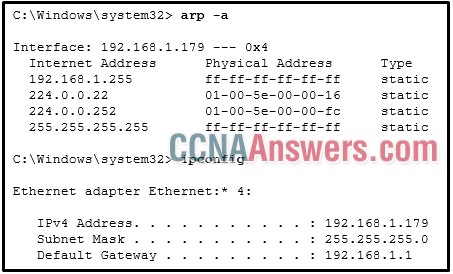
The default gateway device cannot be contacted.
The network cable is unplugged.
The DNS server address is not configured.
The subnet mask is configured incorrectly.
The IP configuration is incorrect.
9. Which two WAN technologies are more likely to be used by a business than by teleworkers or home users? (Choose two.)
Frame Relay
VPN
MetroE
cable
DSL
10. Refer to the exhibit. A network administrator is configuring the PPP link between the routers R1 and R2. However, the link cannot be established. Based on the partial output of the show running-config command, what is the cause of the problem?
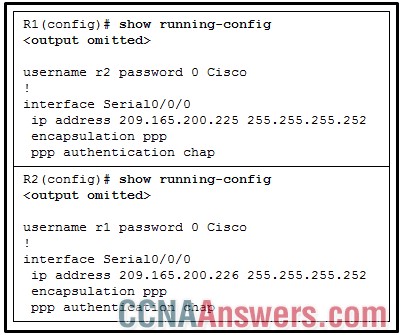
The usernames do not match each other.
The usernames do not match the host names.
The passwords for CHAP should be in lowercase.
The username r1 should be configured on the router R1 and the username r2 should be configured on the router R2.
11. What function is provided by Multilink PPP?
creating one logical link between two LAN switches via the use of multiple physical links
spreading traffic across multiple physical WAN links
enabling traffic from multiple VLANs to travel over a single Layer 2 link
dividing the bandwidth of a single link into separate time slots
12. What is the function of a QoS trust boundary?
A trust boundary identifies the location where traffic cannot be remarked.
A trust boundary only allows traffic to enter if it has previously been marked.
A trust boundary identifies which devices trust the marking on packets that enter a network.
A trust boundary only allows traffic from trusted endpoints to enter the network.
13. In the creation of an IPv6 ACL, what is the purpose of the implicit final command entries, permit icmp any any nd-na and permit icmp any any nd-ns?
to allow forwarding of IPv6 multicast packets
to allow automatic address configuration
to allow IPv6 to MAC address resolution
to allow forwarding of ICMPv6 packets
14. Which statement best describes a WAN?
A WAN is a LAN that is extended to provide secure remote network access.
A WAN is a public utility that enables access to the Internet.
WAN is another name for the Internet.
A WAN interconnects LANs over long distances.
15. Which statement describes a characteristic of dense wavelength division multiplexing (DWDM)?
It enables bidirectional communications over one pair of copper cables.
It supports the SONET standard, but not the SDH standard.
It assigns incoming electrical signals to specific frequencies.
It can be used in long-range communications, like connections between ISPs.
16. Which IPv4 address range covers all IP addresses that match the ACL filter specified by 172.16.2.0 with wildcard mask 0.0.1.255?
172.16.2.0 to 172.16.3.255
172.16.2.1 to 172.16.255.255
172.16.2.0 to 172.16.2.255
172.16.2.1 to 172.16.3.254
17. Which feature sends simulated data across the network and measures performance between multiple network locations?
IP SLA
syslog
SPAN
LLDP
18. Which two pieces of information should be included in a logical topology diagram of a network? (Choose two.)
device type
interface identifier
connection type
cable specification
cable type and identifier
OS/IOS version
19. Refer to the exhibit. A network administrator has configured routers RTA and RTB, but cannot ping from serial interface to serial interface. Which layer of the OSI model is the most likely cause of the problem?
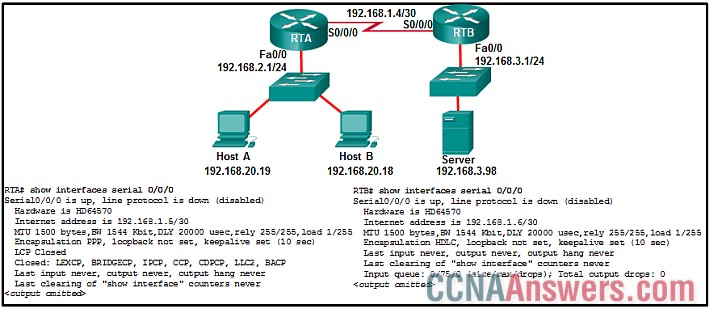
network
physical
data link
transport
application
20. What are two characteristics of video traffic? (Choose two.)
Video traffic requires a minimum of 30 kbs of bandwidth.
Video traffic latency should not exceed 400 ms.
Video traffic is more resilient to loss than voice traffic is.
Video traffic consumes less network resources than voice traffic consumes.
Video traffic is unpredictable and inconsistent.
21. In configuring SNMPv3, what is the purpose of creating an ACL?
to define the type of traffic that is allowed on the management network
to specify the source addresses allowed to access the SNMP agent
to define the protocols allowed to be used for authentication and encryption
to define the source traffic that is allowed to create a VPN tunnel
22. Refer to the exhibit. The IPv6 access list LIMITED_ACCESS is applied on the S0/0/0 interface of R1 in the inbound direction. Which IPv6 packets from the ISP will be dropped by the ACL on R1?
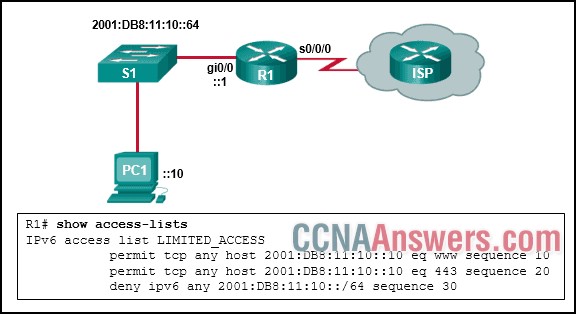
ICMPv6 packets that are destined to PC1
packets that are destined to PC1 on port 80
neighbor advertisements that are received from the ISP router
HTTPS packets to PC1
23. Connecting offices at different locations using the Internet can be economical for a business. What are two important business policy issues that should be addressed when using the Internet for this purpose? (Choose two.)
privacy
security
addressing
bandwidth
WAN technology
24. Refer to the exhibit. What is the network administrator verifying when issuing the show ip interface brief command on R1 in respect to the PPPoE connection to R2?
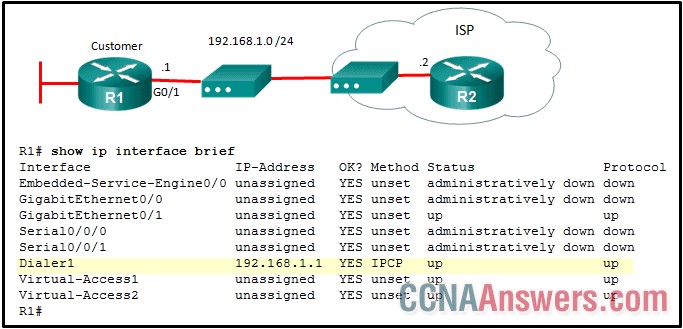
that the IP address on R1 G0/1 is in the same network range as the DSL modem
that the Dialer1 interface has been assigned an IP address by the ISP router
that the Dialer1 interface is up and up
that the Dialer1 interface has been manually assigned an IP address
25. Which QoS mechanism allows delay-sensitive data, such as voice, to be sent first before packets in other queues are sent?
LLQ
FIFO
CBWFQ
FCFS
26. How many DS0 channels are bundled to produce a 1.544 Mbps T1 line?
2
24
28
12
27. Which technology requires the use of PPPoE to provide PPP connections to customers?
T1
dialup analog modem
DSL
dialup ISDN modem
28. Which technology creates a mapping of public IP addresses for remote tunnel spokes in a DMVPN configuration?
ARP
Ipsec
NAT
NHRP
29. Refer to the exhibit. A named access list called chemistry_block has been written to prevent users on the Chemistry Network and public Internet from access to Records Server. All other users within the school should have access to this server. The list contains the following statements:
deny 172.16.102.0 0.0.0.255 172.16.104.252 0.0.0.0
permit 172.16.0.0 0.0.255.255 172.16.104.252 0.0.0.0
Which command sequence will place this list to meet these requirements?
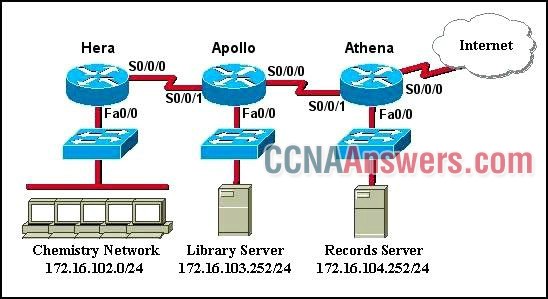
Athena(config)# interface fa0/0
Athena(config-if)# ip access-group chemistry_block out
Apollo(config)# interface s0/0/0
Apollo(config-if)# ip access-group chemistry_block out
Hera(config)# interface fa0/0
Hera(config-if)# ip access-group chemistry_block in
Hera(config)# interface s0/0/0
Hera(config-if)# ip access-group chemistry_block out
Apollo(config)# interface s0/0/1
Apollo(config-if)# ip access-group chemistry_block in
Athena(config)# interface s0/0/1
Athena(config-if)# ip access-group chemistry_block in
30. Match OoS techniques with the description. (Not all options are used.)
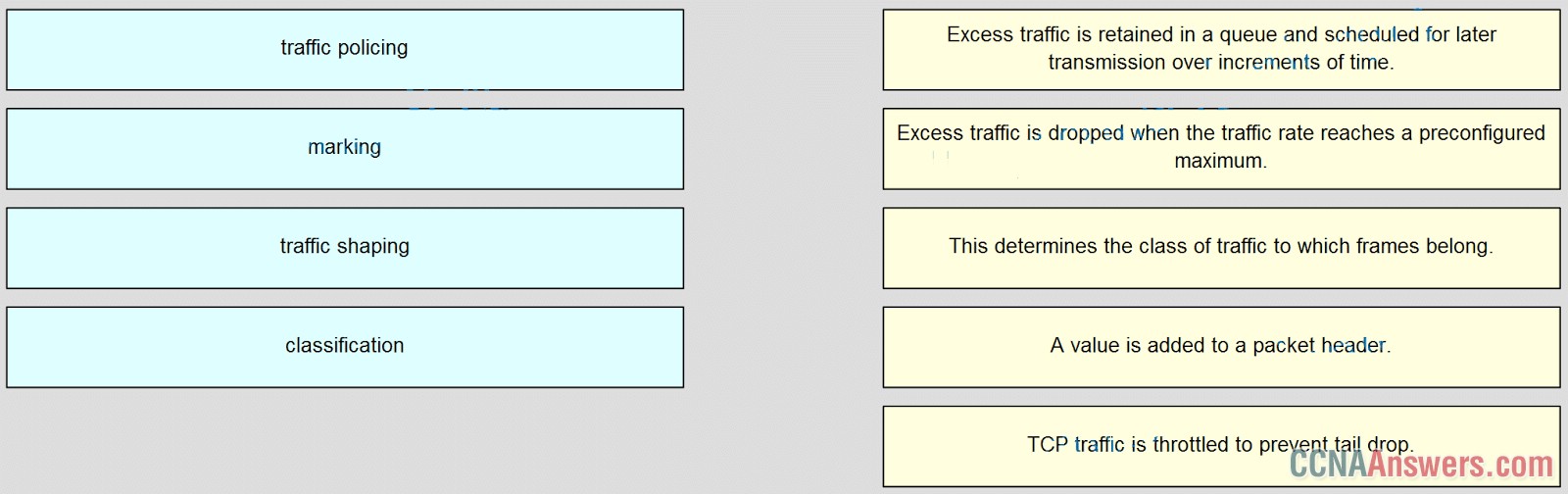
Excess traffic is retained in a queue and scheduled for later transmission over increments of time -> traffic shaping
Excess traffic is dropped when the traffic rate reaches a preconfigured maximum -> traffic policing
This determines the class of traffic to which frames belong -> classification
A value is added to a packer header -> marking
31. A data center has recently updated a physical server to host multiple operating systems on a single CPU. The data center can now provide each customer with a separate web server without having to allocate an actual discrete server for each customer. What is the networking trend that is being implemented by the data center in this situation?
Maintaining communication integrity
online collaboration
BYOD
virtualization
32. Refer to the exhibit. All routers are successfully running the BGP routing protocol. How many routers must use EBGP in order to share routing information across the autonomous systems?
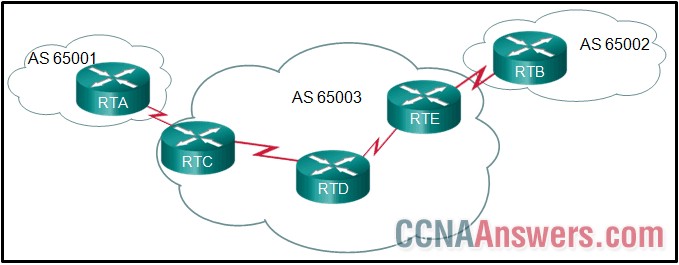
5
2
4
3
33. Which Cisco feature sends copies of frames entering one port to a different port on the same switch in order to perform traffic analysis?
HIPS
CSA
SPAN
VLAN
34. Which network performance statistics should be measured in order to verify SLA compliance?
the number of error messages that are logged on the syslog server
latency, jitter, and packet loss
NAT translation statistics
device CPU and memory utilization
35. What is a disadvantage of a packet-switched network compared to a circuit-switched network?
higher cost
less flexibility
higher latency
fixed capacity
36. Which Cloud computing service would be best for a new organization that cannot afford physical servers and networking equipment and must purchase network services on-demand?
PaaS
ItaaS
SaaS
IaaS
37. Refer to the exhibit. What is used to exchange routing information between routers within each AS?
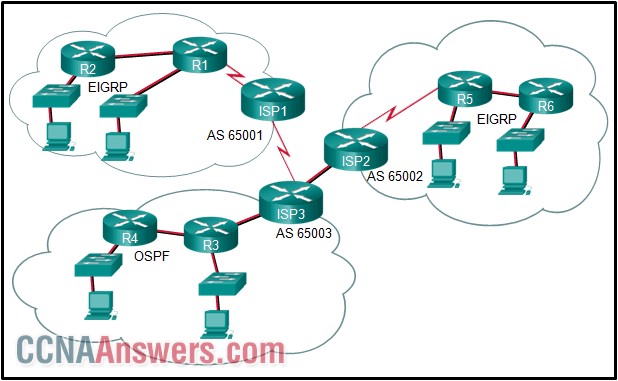
EGP routing protocols
default routing
IGP routing protocols
static routing
38. Refer to the exhibit. What feature does an SNMP manager need in order to be able to set a parameter on switch ACSw1?
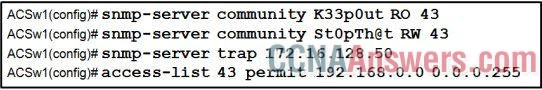
a manager who is using an SNMP string of K44p0ut
a manager who is using authPriv
a manager who is using host 192.168.0.5
a manager who is using an Inform Request MIB
39. A network administrator is configuring a PPP link with the commands:
R1(config-if)# encapsulation ppp
R1(config-if)# ppp quality 70
What is the effect of these commands?
The PPP link will not be established if more than 30 percent of options cannot be accepted.
The NCP will send a message to the sending device if the link usage reaches 70 percent.
The LCP establishment phase will not start until the bandwidth reaches 70 percent or more.
The PPP link will be closed down if the link quality drops below 70 percent.
40. Which term describes the role of a Cisco switch in the 802.1X port-based access control?
supplicant
authentication server
authenticator
agent
41. What advantage does DSL have compared to cable technology?
DSL has no distance limitations.
DSL upload and download speeds are always the same.
DSL is not a shared medium.
DSL is faster.
42. What is a secure configuration option for remote access to a network device?
Configure Telnet.
Configure an ACL and apply it to the VTY lines.
Configure 802.1x.
Configure SSH.
43. Which broadband technology would be best for a user that needs remote access when traveling in mountains and at sea?
Mobile broadband
Wi-Fi Mesh
WiMax
satellite
44. Which type of QoS marking is applied to Ethernet frames?
DSCP
ToS
IP precedence
CoS
45. A company is considering updating the campus WAN connection. Which two WAN options are examples of the private WAN architecture? (Choose two.)
cable
municipal Wi-Fi
Ethernet WAN
leased line
digital subscriber line
46. Which component of the ACI architecture translates application policies into network programming?
the Application Network Profile endpoints
the hypervisor
the Application Policy Infrastructure Controller
the Nexus 9000 switch
47. Which pillar of the Cisco IoT System allows data to be analyzed and managed at the location where it is generated?
fog computing
application enhancement platform
network connectivity
data analytics
48. A corporation is searching for an easy and low cost solution to provide teleworkers with a secure connection to headquarters. Which solution should be selected?
dial-up connection
remote access VPN over the Internet
site-to-site VPN over the Internet
leased line connection
49. A vibration sensor on an automated production line detects an unusual condition. The sensor communicates with a controller that automatically shuts down the line and activates an alarm. What type of communication does this scenario represent?

people-to-machine
people-to-people
machine-to-machine
machine-to-people
50. Which WAN technology can serve as the underlying network to carry multiple types of network traffic such as IP, ATM, Ethernet, and DSL?
Frame Relay
Ethernet WAN
ISDN
MPLS
51. The security policy in a company specifies that the staff in the sales department must use a VPN to connect to the corporate network to access the sales data when they travel to meet customers. What component is needed by the sales staff to establish a remote VPN connection?
VPN concentrator
VPN appliance
VPN gateway
VPN client software
52. What guideline is generally followed about the placement of extended access control lists?
They should be placed as close as possible to the destination of the traffic to be denied.
They should be placed as close as possible to the source of the traffic to be denied.
They should be placed on the fastest interface available.
They should be placed on the destination WAN link.
53. What is used to pre-populate the adjacency table on Cisco devices that use CEF to process packets?
the FIB
the ARP table
the DSP
the routing table
54. A network administrator is testing IPv6 connectivity to a web server. The network administrator does not want any other host to connect to the web server except for the one test computer. Which type of IPv6 ACL could be used for this situation?
a standard or extended ACL
only an extended ACL
only a named ACL
an extended, named, or numbered ACL
only a standard ACL
55. Refer to the exhibit. As traffic is forwarded out an egress interface with QoS treatment, which congestion avoidance technique is used?
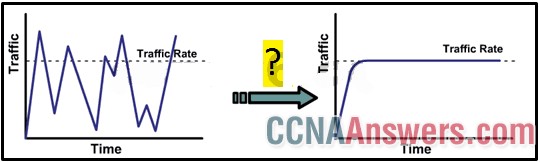
weighted random early detection
traffic policing
traffic shaping
classification and marking


Leave a Reply