CCNA 1 Chapter 4 V6.0 Answers
1. Refer to the exhibit. What is wrong with the displayed termination?

The wires are too thick for the connector that is used.
The untwisted length of each wire is too long.
The woven copper braid should not have been removed.
The wrong type of connector is being used.
2. Why are two strands of fiber used for a single fiber optic connection?
They prevent crosstalk from causing interference on the connection.
They increase the speed at which the data can travel.
The two strands allow the data to travel for longer distances without degrading.
They allow for full-duplex connectivity.
3. Refer to the exhibit. Which statement describes the media access control methods that are used by the networks in the exhibit?
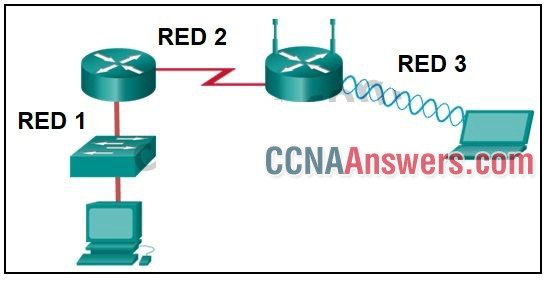
All three networks use CSMA/CA
Network 1 uses CSMA/CD and Network 3 uses CSMA/CA.
Network 1 uses CSMA/CA and Network 2 uses CSMA/CD.
Network 2 uses CSMA/CA and Network 3 uses CSMA/CD.
None of the networks require media access control.
4. Fill in the blank.
A physical topology that is a variation or combination of a point-to-point, hub and spoke, or mesh topology is commonly known as a _hybrid_ topology.
5. Which method of data transfer allows information to be sent and received at the same time?
full duplex
simplex
multiplex
half duplex
6. What is one advantage of using fiber optic cabling rather than copper cabling?
It is able to be installed around sharp bends.
It is usually cheaper than copper cabling.
It is able to carry signals much farther than copper cabling.
It is easier to terminate and install than copper cabling.
7. Match the characteristics to the correct type of fiber. (Not all options are used.)
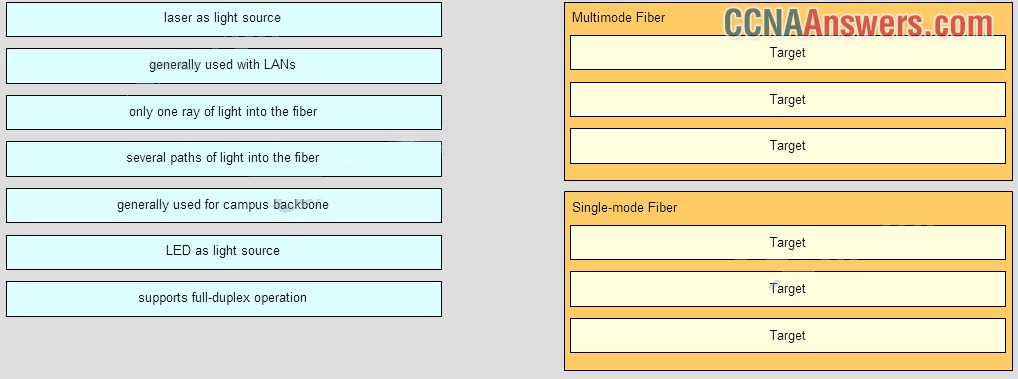
- Multimode Fiber
LED as light source
several paths of light into the fiber
generally used with LANs
- Single-mode Fiber
only one ray of light into the fiber
generally used for campus backbone
laser as light source
8. What is contained in the trailer of a data-link frame?
Logical address
data
physical address
error detection
9. What are two services performed by the data link layer of the OSI model? (Choose two.)
It accepts Layer 3 packets and encapsulates them into frames.
It determines the path to forward packets.
It encrypts data packets.
It monitors the Layer 2 communication by building a MAC address table.
It provides media access control and performs error detection.
10. Refer to the exhibit. The PC is connected to the console port of the switch. All the other connections are made through FastEthernet links. Which types of UTP cables can be used to connect the devices?
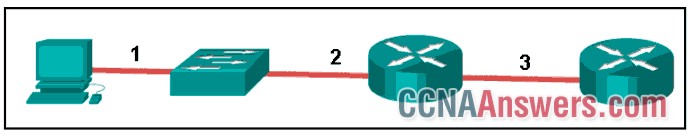
1 – rollover, 2 – crossover, 3 – straight-through
1 – crossover, 2 – rollover, 3 – straight-through
1 – rollover, 2 – straight-through, 3 – crossover
1 – crossover, 2 – straight-through, 3 – rollover
11. Which type of connector does a network interface card use?
PS-2
DIN
RJ-11
RJ-45
12. A network administrator is designing the layout of a new wireless network. Which three areas of concern should be accounted for when building a wireless network? (Choose three.)
interference
packet collision
security
mobility options
coverage area
extensive cabling
13. What is indicated by the term throughput?
the measure of the usable data transferred across the media
the measure of the bits transferred across the media over a given period of time
the time it takes for a message to get from sender to receiver
the capacity of a particular medium to carry data
the guaranteed data transfer rate offered by an ISP
14. What is the function of the CRC value that is found in the FCS field of a frame?
To compute the checksum header for the data field in the frame
to verify the logical address in the frame
to verify the physical address in the frame
to verify the integrity of the received frame
15. What technique is used with UTP cable to help protect against signal interference from crosstalk?
wrapping a foil shield around the wire pairs
twisting the wires together into pairs
terminating the cable with special grounded connectors
encasing the cables within a flexible plastic sheath
16. Which characteristic describes crosstalk?
the distortion of the transmitted messages from signals carried in adjacent wires
the loss of wireless signal over excessive distance from the access point
the weakening of the network signal over long cable lengths
the distortion of the network signal from fluorescent lighting
17. As data travels on the media in a stream of 1s and 0s how does a receiving node identify the beginning and end of a frame?
The transmitting node inserts start and stop bits into the frame.
The receiving node identifies the beginning of a frame by seeing a physical address.
The transmitting node sends a beacon to notify that a data frame is attached.
The transmitting node sends an out-of-band signal to the receiver about the beginning of the frame.
18. A network administrator notices that some newly installed Ethernet cabling is carrying corrupt and distorted data signals. The new cabling was installed in the ceiling close to fluorescent lights and electrical equipment. Which two factors may interfere with the copper cabling and result in signal distortion and data corruption? (Choose two.)
extended length of cabling
signal attenuation
RFI
EMI
crosstalk
19. What is true concerning physical and logical topologies?
Physical topologies are concerned with how a network transfers frames.
Physical topologies display the IP addressing scheme of each network.
The logical topology is always the same as the physical topology.
Logical topologies refer to how a network transfers data between devices.
20. Which statement describes an extended star topology?
End devices are connected together by a bus and each bus connects to a central intermediate device.
All end and intermediate devices are connected in a chain to each other.
End devices connect to a central intermediate device, which in turn connects to other central intermediate devices.
Each end system is connected to its respective neighbor via an intermediate device.
21. Which layer of the OSI model is responsible for specifying the encapsulation method used for specific types of media?
data link
physical
transport
application
22. Fill in the blank.
The term _bandwidth_ indicates the capacity of a medium to carry data and it is typically measured in kilobits per second (kb/s) or megabits per second (Mb/s).
23. What are two reasons for physical layer protocols to use frame encoding techniques? (Choose two.)
to identify where the frame starts and ends
to reduce the number of collisions on the media
to provide better media error correction
to increase the media throughput
to distinguish data bits from control bits
24. Fill in the blank.
What acronym is used to reference the data link sublayer that identifies the network layer protocol encapsulated in the frame? LLC


Leave a Reply