CCNA 4 Chapter 2 V4.0 Answers
1.
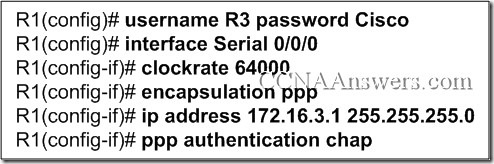
Refer to the exhibit. Router R1, the DCE device, has just been configured for PPP encapsulation with authentication. What series of commands will allow another router, the DTE device, to communicate over its serial 0/0/0 interface to router R1?
Router(config)# hostname R3
R3(config)# username R1 password Cisco
R3(config)# interface Serial 0/0/0
R3(config-if)# encapsulation ppp
R3(config-if)# ip address 172.16.3.3 255.255.255.0
R3(config-if)# ppp authentication chap
Router(config)# hostname R3
R3(config)# username R3 password Cisco
R3(config)# interface Serial 0/0/0
R3(config-if)# encapsulation ppp
R3(config-if)# ip address 172.16.3.3 255.255.255.0
R3(config-if)# ppp authentication chap
Router (config)# username Router password Cisco
Router (config)# interface Serial 0/0/0
Router (config-if)# clockrate 64000
Router (config-if)# encapsulation ppp
Router (config-if)# ip address 172.16.3.1 255.255.255.0
Router config-if)# ppp authentication chap
Router (config)# username R1 password Cisco
Router config)# interface Serial 0/0/0
Router (config-if)# clockrate 64000
Router config-if)# encapsulation ppp
Router (config-if)# ip address 172.16.3.1 255.255.255.0
Router (config-if)# ppp authentication chap
2. Which serial communications DTE/DCE interface standard is used to provide high-speed connectivity of up to 52 Mbps between LANs and is found on many high-end Cisco routers?
EIA/TIA 232 (RS-232)
EIA/TIA 422 (RS-422)
EIA/TIA 423 (RS-423)
EIA/TIA-612/613 (HSSI)
ITU V.35