CCNA 1 Practice Final Exam Answer V3.1
1. When a network administrator applies the subnet mask 255.255.255.248 to a Class A address, for any given subnet, how many IP addresses are available to be assigned to devices?
1022
510
254
126
30
6
2. What is the maximum distance that 10BASE-T will transmit data before signal attenuation affects the data delivery?
100 meters
185 meters
300 meters
500 meters
3. What are features of the TCP/IP Transport layer? (Choose two.)
path determination
handles representation, encoding and dialog control
uses TCP and UDP protocols
packet switching
reliability, flow control and error correction
4. "CompA" is trying to locate a new computer named "CompB" on the network. Which of the following does "CompA" broadcast to find the MAC address of "CompB"?
MAC request
ARP request
ping
Telnet
proxy ARP
5. Which term describes an ARP response by a router on behalf of a requesting host?
ARP
RARP
Proxy ARP
Proxy RARP
6. Which type of institution does the domain suffix .org represent?
government
education
network
non-profit
7. Using the data transfer calculation T=S/BW, how long would it take a 4MB file to be sent over a 1.5Mbps connection?
52.2 seconds
21.3 seconds
6.4 seconds
2 seconds
0.075 seconds
0.0375 seconds
8. Which of the following are features of the Internet Protocol (IP)? (Choose two.)
It is the most widely implemented global addressing scheme.
It allows two hosts to share a single address on a local area network.
It is a hierarchical addressing scheme allowing addresses to be grouped.
It is only locally significant, used primarily on local area networks.
9. Which of the following are small, discrete components found within a personal computer? (Choose three.)
transistor
microprocessor
power supply
capacitor
light emitting diode
hard disk
10. Which part of an IP address identifies a specific device on a network?
first two octets
third and fourth octets
network portion
host portion
only the fourth octet
11. In a new network installation, the network administrator has decided to use a medium that is not affected by electrical noise. Which cable type will best meet this standard?
coaxial
screened twisted pair
shielded twisted pair
unshielded twisted pair
fiber optic
12. Which OSI layer defines the functions of a router?
physical
data link
network
transport
session
13. Which part of the URL http://www.ccnaanswers.com/about gives the name of the domain?
www
http://
/about
ccnaanswers.com
14. Which layer of the OSI model covers physical media?
Layer 1
Layer 2
Layer 3
Layer 4
Layer 5
Layer 6
15. To make sure timing limitations are not violated when implementing a 10 Mbps Ethernet network involving hubs or repeaters, a technician should adhere to which rule?
the 4-5-3 rule
the 6-4-2 rule
the 3-4-5 rule
the 5-4-3 rule
16. Which of these workstation installation and setup tasks are concerned with network access layer functions? (Choose two.)
configuring the e-mail client
installing NIC drivers
configuring IP network settings
connecting the network cable
using FTP to download application software updates
17. During cable testing, which of the following are used to calculate the information carrying capacity of a data cable? (Choose two.)
bit speed
attenuation
wire map
saturation limit
analog bandwidth
18. A small company has a class C network license and needs to create five usable subnets, each subnet capable of accommodating at least 20 hosts. Which of the following is the appropriate subnet mask?
255.255.255.0
255.255.255.192
255.255.255.224
255.255.255.240
19. Which of the following describes the use of Spanning Tree Protocol (STP)?
resolve routing loops
eliminate Split Horizon errors
limit collisions
resolve switching loops
20. What is important to remember about the data link layer of the OSI model when considering Peer to Peer communication? (Choose three.)
It links data to the transport layer.
It encapsulates frames into packets.
It provides a service to the network layer.
It encapsulates the network layer information into a frame.
Its header contains a physical address which is required to complete the data link functions.
It encodes the data link frame into a pattern of 1s and 0s (bits) for transmission on the medium.
21. Which protocol functions at the internet layer of the TCP/IP protocol suite?
File Transfer Protocol (FTP)
Trivial File Transfer Protocol (TFTP)
Transmission Control Protocol (TCP)
Internet Protocol (IP)
User Datagram Protocol (UDP)
Simple Mail Transport Protocol (SMTP)
22. What is the recommended maximum number of workstations configured on a peer-to-peer network?
25
15
10
5
2
23. What type of network cable is used between a terminal and a console port?
cross-over
straight-through
rollover
patch cable
24. Which OSI layer encapsulates data into packets?
session
transport
network
data link
25. The highest capacity Ethernet technologies should be implemented in which areas of a network? (Choose three.)
between workstation and backbone switch
between individual workstations
between backbone switches
between enterprise server and switch
on aggregate access links
26. Select the necessary information that is required to compute the estimated time it would take to transfer data from one location to another. (Choose two.)
file size
data format
network in use
type of medium
bandwidth of the link
27. Which of the following services is used to translate a web address into an IP address?
DNS
WINS
DHCP
Telnet
28. Which of the following does 1000BASE-T use to accomplish gigabit speeds on Cat 5e cable?
the use of four conductors in full-duplex mode
the use of two multiplexed pairs of wires, simultaneously
the use of three pairs of wires for data and the fourth for stabilization and forward error correction
the use of all four pairs of wires in full-duplex mode, simultaneously
29. John has been hired as the network administrator of a local company and has decided to add more hubs to the company's existing network. Which of the following has been caused by John's inexperience?
collision domain extended
an increased number of collision domains
increased network performance
increased bandwidth
extended bandwidth
30. If a network administrator needed to download files from a remote server, which protocols could the administrator use to remotely access those files? (Choose two.)
ASCII
TFTP
IMAP
FTP
UDP
31. What does the "10" in 10Base2 indicate about this version of Ethernet?
The version uses Base10 numbering within the frames.
The version operates at a transmission rate of 10 Mbps.
Frames can travel 10 meters unrepeated.
The maximum frame length is 10 octets.
32. Which of the following protocols are used for e-mail transfer between clients and servers? (Choose three.)
TFTP
SNMP
POP3
SMTP
IMAP4
postoffice
33. Convert the Hexadecimal number A2 into its Base 10 equivalent. Select the correct answer from the list below.
156
158
160
162
164
166
34. Convert the binary number 10111010 into its hexadecimal equivalent. Select the correct answer from the list below.
85
90
BA
A1
B3
1C
35. An ISDN Basic Rate Interface (BRI) is composed of how many signaling channels?
1
2
3
4
36. Which combinations of charges will be repelled by electric force? (Choose two.)
neutral and neutral
neutral and positive
neutral and negative
positive and positive
positive and negative
negative and negative
37. What device must be used between an AUI port of a networking device and the media to which it is being connected?
a transducer
a transmitter
a transceiver
a transponder
a port replicator
38. For which of the following is Ethernet considered the standard? (Choose three.)
inter-building connection
mid-length voice
video conferencing
vertical wiring
horizontal wiring
diagonal wiring
39. Which of the following is a term associated with replacing hubs with switches to increase the number of collision domains?
encapsulation
latency
segmentation
layered model
broadcast domain
extended
40. What is established during a connection-oriented file transfer between computers? (Choose two.)
a temporary connection to establish authentication of hosts
a connection used for ASCII or binary mode data transfer
a connection used to provide the tunnel through which file headers are transported
a command connection which allows the transfer of multiple commands directly to the remote server system
a control connection between the client and server
41. A company with a Class B license needs to have a minimum of 1,000 subnets with each subnet capable of accommodating 50 hosts. Which mask below is the appropriate one?
255.255.0.0
255.255.240.0
255.255.255.0
255.255.255.192
255.255.255.224
42. The accumulation of traffic from which of the following can cause a network condition called broadcast radiation? (Choose three.)
anonymous FTP servers
telnet sessions
video over IP applications
NAS services
ARP requests
RIP updates
43. How is a MAC address represented?
four groups of eight binary digits separated by a decimal point
four Base10 digits separated by a decimal point
six hexadecimal digits
twelve hexadecimal digits
twenty-four Base10 digits
44. Which of the following items are common to all 100BASE technologies? (Choose three.)
frame format
media
connectors
timing
multi-part encoding
45. Which of the following wireless standards increased transmission capabilities to 11 Mbps?
802.11a
802.11b
802.11c
802.11d
46.
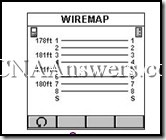
What type of wiring problem is depicted in this sample of a cable tester?
a fault
a short
an open
a split
a good map
47. Which of the following will test the internal loopback of a node?
ping 10.10.10.1
ping 192.168.1.1
ping 127.0.0.1
ping 223.223.223.223
ping 255.255.255.255
48. Which of the following is the Layer 4 PDU?
bit
frame
packet
segment
49. Which of the following are useable Class A IP addresses with a default subnet mask? (Choose three.)
127.0.39.1
111.9.28.30
123.1.2.132
128.50.38.2
105.1.34.1
0.23.92.3
50. Which of the following are considered the best electrical conductors for use in data network communications? (Choose three.)
glass fibers
copper
gold
plastic
silicon
silver


Leave a Reply