CCNA 1 Final Exam Answers 2011
1. Due to a security violation, the router passwords must be changed. What information can be learned from the following configuration entries? (Choose two.)
Router(config)# line vty 0 3
Router(config-line)# password c13c0
Router(config-line)# login
The entries specify three Telnet lines for remote access.
The entries specify four Telnet lines for remote access.
The entries set the console and Telnet password to "c13c0".
Telnet access will be denied because the Telnet configuration is incomplete.
Access will be permitted for Telnet using "c13c0" as the password.
2. Which two actions could be taken by a router if a specific match is not made to a route in the routing table? (Choose two.)
The packet will be discarded.
The packet will be sent back to the source.
The packet will be flooded out all interfaces.
Neighboring routers are polled to find the best path.
The packet will be forwarded to a default route if one is present.
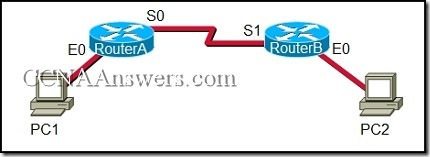
3.
Refer to the exhibit. The network administrator remotely accesses the CLI of RouterB from PC1 using a secure connection. Which statement is true about this connection?
The Telnet server process is running on PC1.
Only the exchange of the Telnet username and password is encrypted.
The GET request is sent to RouterA to retrieve data.
The SSH service is used to connect PC1 to RouterB.
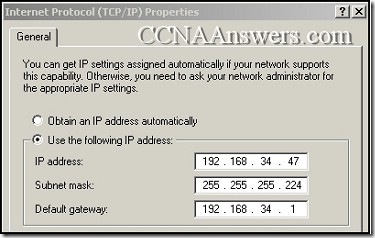
4.
Refer to the exhibit. What three statements are true about the IP configuration that is shown? (Choose three.)
The prefix of the subnet mask is /26.
The network on which this computer resides can have 30 hosts.
The computer is unable to communicate outside of the local network.
The address that is assigned to the computer represents private addressing.
The IP address that is assigned to the computer is routable on the Internet.
The IP address that is assigned as the default gateway is valid for this host.
5. What information can be gathered by using the command netstat?
the default gateway
the routing protocol
active TCP connections
the locally configured subnet mask
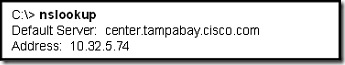
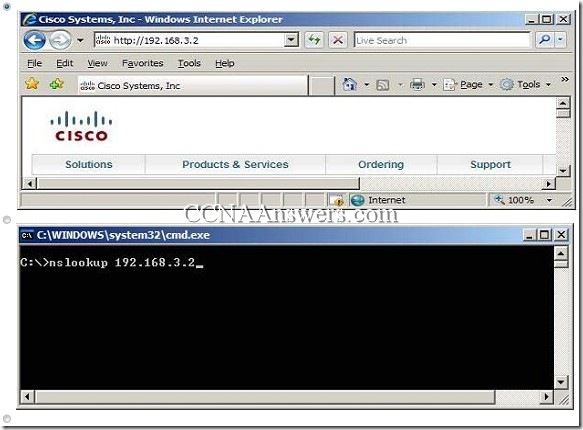
6.
Refer to the exhibit. The nslookup command that is shown was issued on a Windows PC host. What does the 10.32.5.74 address represent?
the IP address of the host
the default gateway for the host
the primary DNS server for the host
the home page address for the host
7.
Refer to the exhibit. A network administrator remotely accesses the CLI of RouterB from PC1 using Telnet. Which statement is true about this connection?
The data is automatically encrypted.
A Telnet server process is running on PC1.
The connection is made through a VTY session on the router.
A GET request was sent to RouterB to retrieve data during this session.
8. Which three addresses are private IP addresses? (Choose three.)
10.0.0.1
46.1.1.88
172.31.31.10
172.32.16.10
192.168.8.8
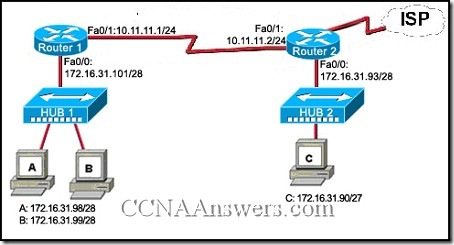
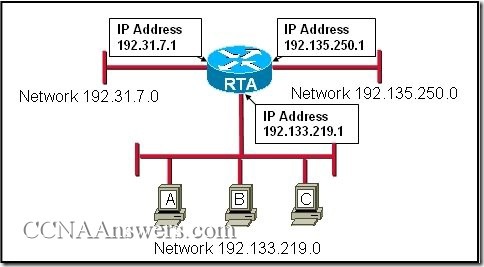
9.
Refer to the exhibit. Host C is able to ping 127.0.0.1 successfully, but is unable to communicate with hosts A and B in the organization. What is the likely cause of the problem?
Hosts A and B are not on the same subnet as host C.
The IP addresses on the router serial interfaces are wrong.
The subnet mask on host C is improperly configured.
The FastEthernet interface fa0/0 of router 1 is wrongly configured.
10. Which OSI layer addressing is required to route packets between two networks?
Layer 1
Layer 2
Layer 3
Layer 4
11. What is the effect of using the Router# copy running-config startup-config command on a router?
The contents of ROM will change.
The contents of RAM will change.
The contents of NVRAM will change.
The contents of flash will change.
12. A PC can not connect to any remote websites, ping its default gateway, or ping a printer that is functioning properly on the local network segment. Which action will verify that the TCP/IP stack is functioning correctly on this PC?
Use the ipconfig /all command at the host’s command prompt.
Use the ping 127.0.0.1 command at the command prompt.
Use the traceroute command at the command prompt to identify any failures on the path to the gateway.
Use FTP to check for connectivity to remote sites.
Download a troubleshooting tool from the PC manufacturer's website.
13. Which subnet mask will allow 2040 hosts per subnet on the IP network 10.0.0.0?
255.255.0.0
255.255.254.0
255.255.252.0
255.255.248.0
255.255.240.0
255.255.255.128
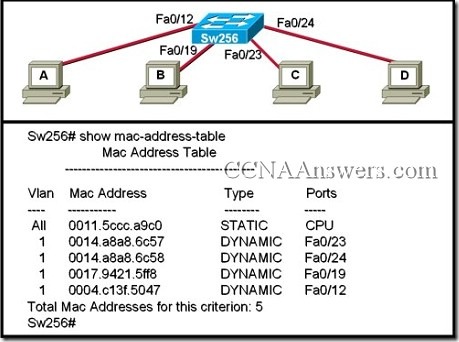
14.
Refer to the exhibit. When computer A sends a frame to computer D, what computers receive the frame?
only computer D
only computer A and computer D
only computer B, computer C, and computer D
all computers
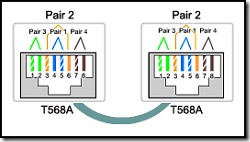
15.
Refer to the exhibit. While configuring a network, a technician wired each end of a Category 5e cable as shown. Which two statements are true about this setup? (Choose two.)
The cable is suitable for connecting a switch to a router Ethernet port.
The cable is suitable for connecting dissimilar types of devices.
The cable is unusable and must be rewired.
The cable is terminated in a way that the transmit pin is wired to the receive pin.
The cable simulates a point-to-point WAN link.
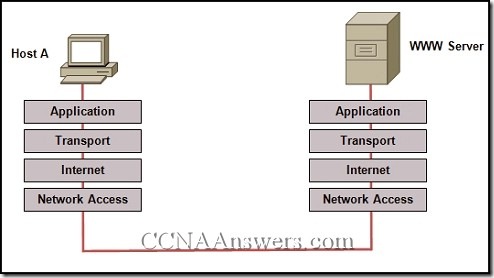
16.
Refer to the exhibit. Which layered network model is shown in the diagram?
Cisco
IETF
OSI
TCP/IP
17. An administrator makes changes to the default configuration of a router and saves them to NVRAM. After testing, it is discovered that the configurations did not have the desired effect and must be removed. What steps must be taken to remove the changes and return the router to the default configuration?
Reboot the router.
Use no version of the commands that are issued.
Issue the erase startup-config command, and then reboot the router.
Issue the erase running-config command, and then reboot the router.
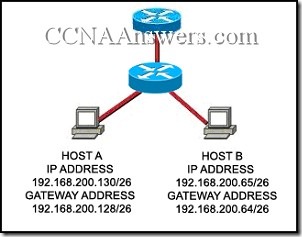
18.
Refer to the exhibit. Host A and B are unable to communicate with each other. What is the reason for this?
Host A is assigned a network address.
Host B is assigned a multicast address.
Host A and host B belong to different networks.
The gateway addresses are network addresses.
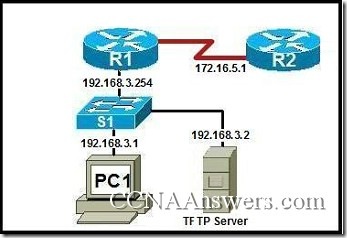
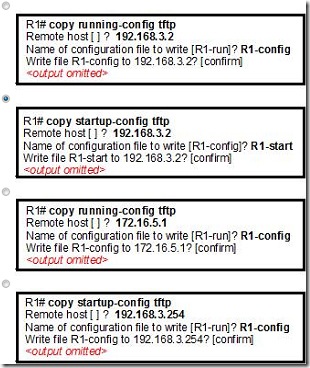
19.
Refer to the exhibit. A network technician has made several changes to R1 since the configuration has last been saved. The modified configuration did not produce the desired changes. The technician wants to store a backup copy of the saved configuration on a TFTP server before reloading. Which action will cause the unmodified data to be saved on the TFTP server?
20. What can the user do from the command prompt, Router(config-line)# ?
Configure one of the network interfaces.
Configure one of the physical or virtual lines.
Verify the running configuration on the device.
Configure the parameters for one of the routing protocols.
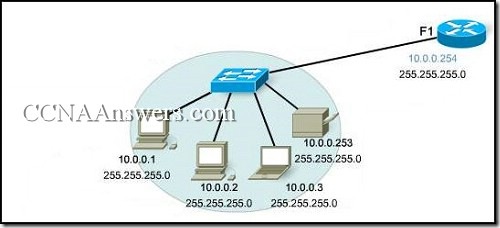
21.
Refer to the exhibit. A PC is connected to a network. Which action will verify that the PC can communicate with its default gateway?
Use the ping 127.0.0.1 command.
Use the ipconfig command.
Use the ipconfig/all command.
Use the ping 10.0.0.254 command.
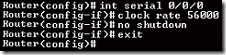
22.
Refer to the exhibit. The serial interface of the router was configured with the use of the commands that are shown. The router cannot ping the router that is directly connected to interface serial 0/0/0. What should the network technician do to solve this problem?
Configure the description at interface serial 0/0/0.
Configure an IP address on interface serial 0/0/0.
Remove the no shutdown command at interface serial 0/0/0
Reboot the router.
23. A technician is asked to secure the privileged EXEC mode of a switch by requiring a password. Which type of password would require this login and be considered the most secure?
console
enable
enable secret
VTY
24. What are two purposes for configuring a banner on a router? (Choose two.)
to announce system downtime
to prevent unauthorized access to the router
to provide a description of interface connections
to assist in legal prosecution for unauthorized access
to provide a welcome message to users who access the router
25.
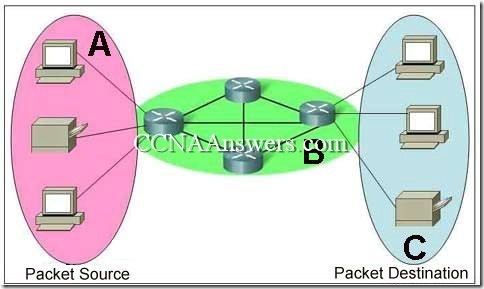
Refer to the exhibit. A PC is communicating with another PC on a remote network. The two networks are connected by three routers. Which action will help to identify the path between the hosts?
Use the ipconfig command at the host.
Use the ipconfig/all command at the destination.
Use the tracert command at the host.
Use the ping command at the destination.
26.
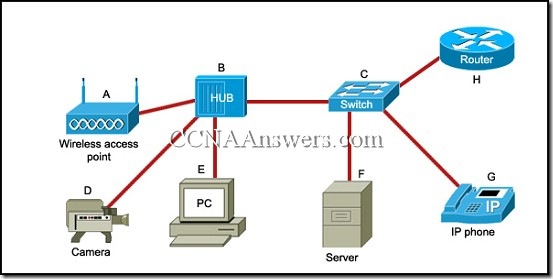
Refer to the exhibit. Which list refers only to end devices?
D,E,F,G
A,H,B,C
A,D,E,F
A,D,E,G
27. When must a router serial interface be configured with the clock rate command?
when the interface is functioning as a DTE device
when the interface timers have been cleared
when the connected DTE device is shut down
when the interface is functioning as a DCE device
28. Which table accurately associates the RFC 1918 private IP addresses with the correct network mask?
29.
Refer to the exhibit. Which two layers of the OSI model describe the same functions as the transport and internet layers of the TCP/IP model? (Choose two.)
application layer
presentation layer
session layer
transport layer
network layer
data link layer
physical layer
30. What happens when a host station receives a frame that contains its own MAC address in the destination field?
The Layer 2 information is removed and the frame is pushed up to Layer 3.
The host station will copy the information to its buffers and send it back out.
The frame originated from the host and will be ignored.
The Layer 3 information is added to the frame.
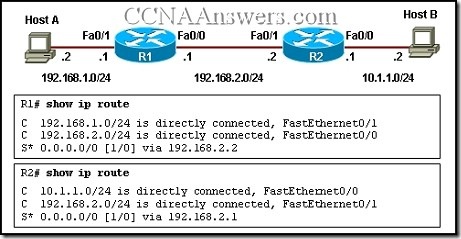
31.
Refer to the exhibit. Host A is configured with the correct IP address for the default gateway of the router R1 FastEthernet0/1 interface. How will a packet that is sent from host A to host B be handled by the devices on the network?
R1 will drop the packet because R1 does not have a specific route in its routing table to the 10.1.1.0/24 network.
R1 will forward the packet to its default gateway, the next hop router R2. R2 will forward the packet to the directly connected network 10.1.1.0/24.
R1 will forward the packet to its default gateway, the next hop router R2. R2 will drop the packet because it does not have a default route to network 10.1.1.0/24.
R1 will forward the packet to its default gateway, the next hop router R2. R2 will drop the packet because it does not have a route that is learned by a routing protocol to network 10.1.1.0/24.
32. What type of network is maintained if a server takes no dedicated role in the network?
mainframe
client/server
peer-to-peer
centralized
33. In a network design project, a network designer needs to select a device to provide collision free connections to 40 hosts on the LAN. Which device should be selected?
hub
router
switch
firewall
34. Which TCP/IP model layer creates additional overhead on network resources due to acknowledgments, tracking, and retransmission of data?
internet
transport
application
network access
35. How many host addresses may be assigned when using the 128.107.0.0 network address with a subnet mask of 255.255.248.0?
30
256
2046
2048
4094
4096
36. Which service is used when the nslookup command is issued on a computer?
FTP
DNS
DHCP
Telnet
37. Which process provides the means to send and receive data when running multiple applications at the same time on a computer?
interleaving
sequencing
segmentation
acknowledgement
38. Which three IPv4 addresses represent valid host addresses for a subnet? (Choose three.)
10.1.12.79/28
10.1.12.113/28
10.1.12.32/28
10.1.11.5/27
10.1.11.97/27
10.1.11.128/27
39. What is the consequence of issuing the erase startup-config command in privileged EXEC mode on a Cisco router?
Data stored in RAM will be removed.
Data stored in NVRAM will be erased.
Information in flash memory will be removed.
Flags in the configuration register will be set to 0.
Both the startup-config and the running-config will be erased.
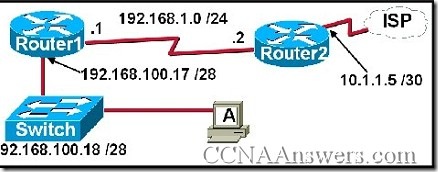
40.
Refer to the exhibit. A network technician is trying to determine the correct IP address configuration for Host A. What is a valid configuration for Host A?
IP address: 192.168.100.19; Subnet Mask: 255.255.255.248; Default Gateway: 192.16.1.2
IP address: 192.168.100.20; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.17
IP address: 192.168.100.21; Subnet Mask: 255.255.255.248; Default Gateway: 192.168.100.18
IP address: 192.168.100.22; Subnet Mask: 255.255.255.240; Default Gateway: 10.1.1.5
IP address: 192.168.100.30; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.1.1
IP address: 192.168.100.31; Subnet Mask: 255.255.255.240; Default Gateway: 192.168.100.18
41. What is the Cisco IOS?
system software for Cisco devices
Read Only Memory in Cisco devices
non-volatile storage for device configurations
an initial operating system that is used for boot functions
42. Which router configuration mode will require user authentication if an administrator issues the enable secret command?
user executive mode
privileged executive mode
global configuration mode
service specific configuration mode
43. Which command or commands will require authentication to access the privileged exec mode?
RTRA(config)# enable secret cisco
RTRA(config)# service password encryption
RTRA(config)# line con 0
RTRA(config-line)# login
RTRA(config-line)# password cisco
RTRA(config)# line vty 0 4
RTRA(config-line)# login
RTRA(config-line)# password cisco
44. A routing issue has occurred in your internetwork. Which of the following type of devices should be examined to isolate this error?
access point
host
hub
router
switch
45. Which statement is true about Layer 3 addresses?
They are physical addresses.
They are used in routing decisions.
They are only used on local networks.
They are altered each time a packet crosses a router.
46.
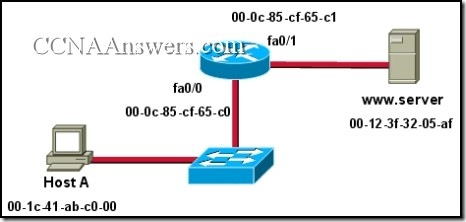
Refer to the exhibit. An administrator on PC1 wants to view some HTML code from a web page housed on the web server. Which client application will allow this request to be started?
47. Which OSI layer does IP rely on to determine whether packets have been lost and to request retransmission?
application
presentation
session
transport
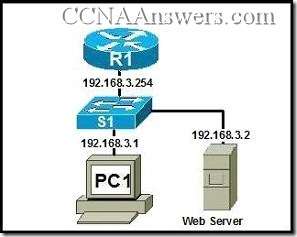
48.
Refer to the exhibit. PC1 is unable to access PC2. To troubleshoot this problem, the technician needs to confirm that the next hop interface is operational. Which default gateway address should the technician ping from PC1 to confirm this?
10.0.0.254
192.168.0.249
192.168.0.250
10.0.1.254
49. An administrator is in the middle of entering a lengthy command when suddenly output from the IOS appears stating that an interface has gone down and then up again. Consequently, the command that the administrator was typing is no longer legible on the terminal. What CLI keystrokes can be entered to return to the line that the administrator was typing?
Ctrl-D
Ctrl-K
Ctrl-R
Ctrl-Z
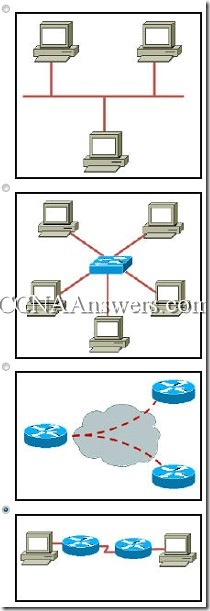
50. Which option represents a point-to-point logical topology diagram?
51. Which physical component is used to access and perform the initial configuration on a new unconfigured router?
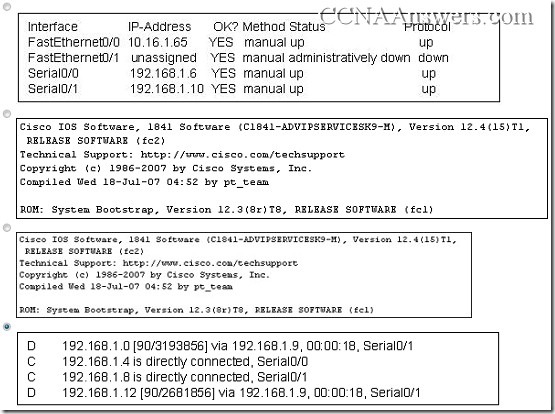
52. Which option shows how a router will route packets to a remote network?










Leave a Reply