CCNA 3 Chapter 1 V4.0 Answers
1. Which layer of the hierarchical network design model is refered to as the high-speed backbone of the internetwork, where high availability and redundancy are critical?
access layer
core layer
data-link layer
distribution layer
network layer
physical layer
2. Which two characteristics are associated with enterprise level switches? (Choose two.)
low port density
high forwarding rate
high latency level
support link aggregation
predefined number of ports
3. Which feature supports higher throughput in switched networks by combining multiple switch ports?
convergence
redundant links
link aggregation
network diameter
4. Which hierarchical design model layer controls the flow of network traffic using policies and delineates broadcast domains by performing routing functions between virtual LANs (VLANs)?
application
access
distribution
network
core
5. What is the likely impact of moving a conventional company architecture to a completely converged network?
Local analog phone service can be completely outsourced to cost-effective providers.
The Ethernet VLAN structure is less complex.
A shared infrastructure is created resulting in a single network to manage.
QoS issues are greatly reduced.
There is less bandwidth competition between voice and video streams.
6.
Refer to the exhibit. Beginning with HR servers and workstations, a network engineer is designing a new security structure for the network. Which set of policies adheres to the hierarchical network model design principles?
Implement Layer 3 switching on S1 to reduce the packet processing load on D1 and D2. Install all security processing on S1 to reduce network traffic load.
Configure port security options on S1. Use Layer 3 access control features on D1 and D2 to limit access to the HR servers to just the HR subnet.
Move all HR assets out of the data center and connect them to S1. Use Layer 3 security functions on S1 to deny all traffic into and out of S1.
Perform all port access and Layer 3 security functions on C1.
7. Which three features are commonly supported at the distribution layer of the Cisco hierarchical network model? (Choose three.)
security policies
Power over Ethernet
switch port security
quality of service
Layer 3 functionality
end user access to network
8. Configuring communication between devices on different VLANs requires the use of which layer of the OSI model?
Layer 1
Layer 3
Layer 4
Layer 5
9. Which layer of the OSI model does an access layer LAN switch use to make a forwarding decision?
Layer 1
Layer 2
Layer 3
Layer 4
10. Which two features are supported at all three levels of the Cisco three-layer hierarchical model? (Choose two.)
Power over Ethernet
load balancing across redundant trunk links
redundant components
Quality of Service
link aggregation
11. A network technician is asked to examine an existing switched network. Following this examination, the technician makes recommendations for adding new switches where needed and replacing existing equipment that hampers performance. The technician is given a budget and asked to proceed. Which two pieces of information would be helpful in determining necessary port density for new switches? (Choose two.)
forwarding rate
traffic flow analysis
expected future growth
number of required core connections
number of hubs that are needed in the access layer to increase performance
12. Which hierarchical design characteristic would be recommended at both the core and distribution layers to protect the network in the case of a route failure?
PoE
redundancy
aggregation
access lists
13. At which heirarchical layer are switches normally not required to process all ports at wire speed?
core layer
distribution layer
access layer
entry layer
14. For organizations that are implementing a voice over IP solution, what functionality should be enabled at all three layers of the hierarchical network?
Power over Ethernet
quality of service
switch port security
inter-VLAN routing
15. A network administrator is selecting a switch that will operate at the network core. Which three features should the switch support for optimum network performance and reliability? (Choose three.)
port security
security policies
10 Gigabit Ethernet
quality of service (QoS)
hot-swappable hardware
Power over Ethernet (PoE)
16. Link aggregation should be implemented at which layer of the hierarchical network?
core only
distribution and core
access and distribution
access, distribution, and core
17. What statement best describes a modular switch?
a slim-line chassis
allows interconnection of switches on redundant backplane
defined physical characteristics
flexible characteristics
18. Which layer of the hierarchical design model provides a means of connecting devices to the network and controlling which devices are allowed to communicate on the network?
application
access
distribution
network
core
19. A technician is attempting to explain Cisco StackWise technology to a client that is setting up three stackable switches. Which explanation accurately describes StackWise technology?
StackWise technology allows up to eight ports to be bound together to increase available bandwidth.
StackWise technology allows the switch to deliver power to end devices by using existing Ethernet cabling.
StackWise technology allows the switch capabilities and ports to be expanded by the addition of line cards.
StackWise technology allows up to nine switches to be interconnected via the use of a fully redundant backplane.
20.
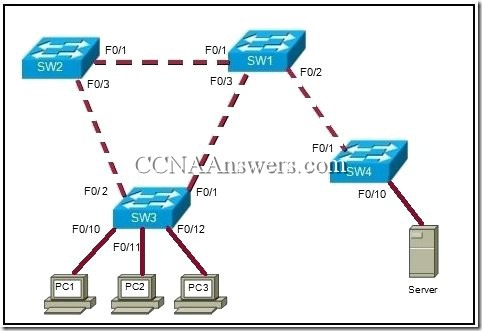
Refer to the exhibit. What characteristic of hierarchical network designs is exhibited by having SW3 connected to both SW1 and Sw2?
scalability
security
redundancy
maintainability



Leave a Reply