CCNA Discovery 1 Final V4.0 Answers
DHomesb Final Exam - CCNA Discovery: Networking for Home and Small Businesses (Version 4.0)
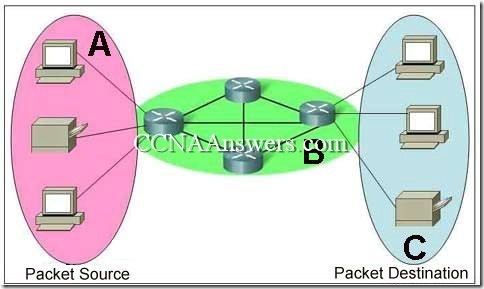
1. What is a function of the distribution layer in the hierarchical design model?
to provide latency free switching
to organize end devices in small manageable groups
to provide connectivity using the high-speed backbone
to provide connectivity between smaller local networks
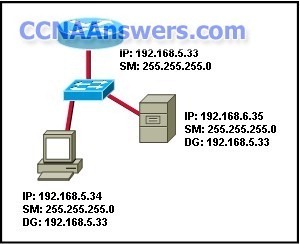
2. Under what circumstance would it be appropriate to use private IP addresses?
for communication between two ISPs
for a network that is directly connected to the Internet
for addresses that are used exclusively within an organization.
for a host with more than one direct connection to the Internet