IT Essentials Chapter 11 V5.0 Answers
1. Which two data storage locations contain persistent data that can be used by computer forensics specialists? (Choose two.)
solid state drives
CPU registers
RAM
hard disk drives
cache
2. Which two actions should a technician take if illegal content, such as child pornography, is discovered on the hard drive of a customer computer? (Choose two.)
Contact a first responder.
Confront the customer immediately.
Shut down the computer until authorities arrive.
Document as much information as possible.
Remove and destroy the hard drive.
3. Which two statements are correct about level one and level two technicians? (Choose two.)
Level two technicians usually respond to the "down calls" as they may be able to resolve them faster.
Level one technicians usually work on the problems that require opening up the computer case.
Level two technicians are often referred to as "incident screeners," and level one technicians are often referred to as "product specialists.
Level two technicians are usually more knowledgeable about technology than the level one technicians are.
Level two technicians prepare a work order and escalate it to a level one technician if a problem cannot be resolved within ten minutes.
4. A technician receives a call from a customer who is too talkative. How should the technician handle the call?
Politely step in and gain control of the call by asking the customer social questions.
Allow the customer to speak without interruption and then try to use closed-ended questions to gather data.
Use open-ended questions and repeat all the information back to the customer to politely show that unnecessary information is being given.
Talk over the customer and quickly gather the necessary information to be of help.
5. Which statement describes a best practice related to time management?
The technician can take the call of another technician, even without permission to do so.
The technician should give better service to a customer for whom the technician feels more sympathy.
The technician should take the easier calls first, regardless of the urgency.
The technician should make sure to call the customer back as close to the callback time as possible.
6. Which two rules pertain to the general daily activities of employees in a call center environment? (Choose two.)
The technician should contact the customer if the technician is going to be late for a follow-up appointment.*
The technician should adjust the work chair to a height that is high enough so that wrists angle downwards toward the keyboard.
The technician should be sure to treat all customers equally.
If a customer complains about another technician, the technician who is taking the call should agree with opinion of the customer.
If a technician takes a call from a customer the technician does not like, the technician should pass the call to another technician.
7. When performing computer forensics, what can be prevented with a properly and carefully documented chain of custody?
identity theft
copying of copyrighted materials
evidence tampering
cyber crime
8. Which situation would require that a support desk call be given the highest priority?
A couple of computers have operating system errors.
The company cannot operate because of a system failure.
Some computers cannot log in to the network.
Two users are requesting an application enhancement.
A user is requesting a RAM memory upgrade.
9. What is a reason to escalate a problem from a level one technician to a level two technician?
when the equipment needs to be rebooted
when the screen resolution of a customer PC needs to be adjusted
when drivers, applications, or operating systems need to be installed
when a peripheral device needs to be replaced
10. What is the correct way to conduct a telephone call to troubleshoot a computer problem?
Always gather information from the customer and escalate the problem.
Ask personal questions to get better acquainted with the customer.
Explain each step to help the customer understand the troubleshooting process.
Maintain professional behavior at all times.
11. What are three pieces of information a level one technician should gather from a customer? (Choose three.)
details of any recent changes to the computer
description of the problem
output from diagnostic software
output from a remote connection to the customer computer
current CMOS settings
contact information
12. What name is given to a certain set of general rules that apply to written communication over the Internet?
flame wars
online interactions
Internet slang
netiquette
13. What customer support procedure would likely cause an upset customer to become more upset?
Ask the customer to do obvious or unnecessary steps.
Reiterate that you want to solve the problem.
Follow a step-by-step approach to solving the problem.
Apologize for the wait time if there has been no wait time.
14. In a computer forensics investigation, which type of data is considered volatile data and can be lost if power is removed from the computer?
data in transit between RAM and the CPU
data stored on an internal drive
data stored on an external drive
data stored on magnetic disks
15. What should a level two technician do immediately after receiving an escalated work order from a level one technician?
Call the customer back to ask any additional questions and resolve the problem.
Call the level one technician and ask questions about the problem.
Document suggestions to solve the problem in the work order and return it to the level one technician.
Send the work order to a level three technician and ask for support.
16. During the process of troubleshooting, a technician gains access to customer private information. What is expected that the technician do with this information?
Send this information to the manager of the customer.
Back up the information just in case the customer needs it some day.
Document all information in a log file.
Send this information to the technician manager.
Keep it confidential.
17. What is the definition of cyber law?
a single law defining criminal acts that are committed online
a contract that defines expectations between and organization and IT service vendors for an agreed upon level of support
the process of collecting and analyzing data from computer systems, networks, wireless communications, and storage devices
the collection of international, country, and local laws that affect computer security professionals
18. What are two sections that are usually included in an SLA? (Choose two.)
supported equipment and software
home contact information of the technician
service provider part suppliers
time of service availability
contact information of other clients
19. What are two examples of displaying professional communication skills while talking to a customer? (Choose two.)
focusing on what you cannot do to give customers an idea of the magnitude of the problem
clarifying what customers say after they have finished their explanations
interrupting customers with a question to gather more information
asking customers to paraphrase their explanations
the use of active listening, with occasional interjections such as "I see" or "I understand"
20. A customer calls to report a computer problem. Which two actions can the technician take to establish a good rapport with the customer? (Choose two.)
Use technical terms to determine the level of knowledge the customer possesses.
Allow the customer to speak without interruption.
Personalize the call by periodically asking questions unrelated to the computer problem.
Refer to the customer by name whenever possible.
Ask only closed-ended questions.
21. When performing computer forensics what is required to prove a chain of custody?
an admission of guilt
collected evidence
proper documentation procedures
expert testimony
22.
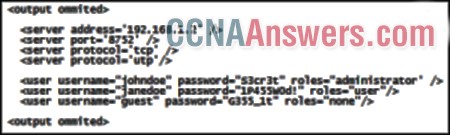
Refer to the exhibit. During the troubleshooting of software that is installed on a computer system, a level one technician requires help from a level two technician. The file shown in the exhibit must be sent to the level two technician. How should the level one technician deliver this file?
Send the file as it is to the level two technician.
Deliver the file in printed format only.
Replace all passwords in the file with before emailing the file and then supply the passwords by secure means, if required.
This file should not be shared with the level two technician.



Leave a Reply