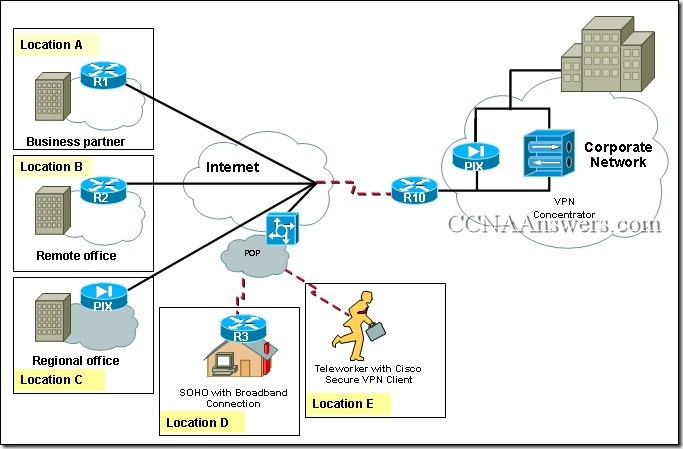
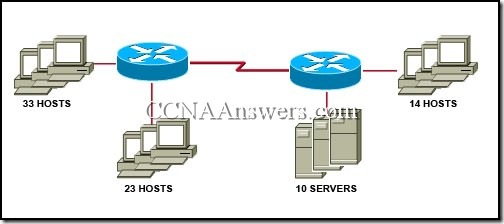
1. What are the steps which must be completed in order to enable inter-VLAN routing using router-on-a-stick?
Configure the physical interfaces on the router and enable a routing protocol.
Create the VLANs on the router and define the port membership assignments on the switch.
Create the VLANs on the switch to include port membership assignment and enable a routing protocol on the router.
Create the VLANs on the switch to include port membership assignment and configure subinterfaces on the router matching the VLANs.
2.
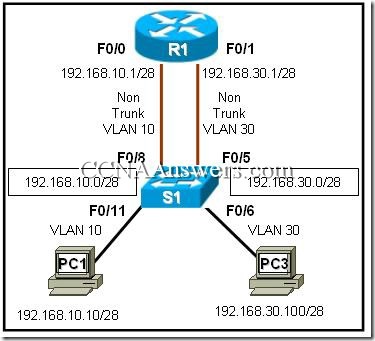
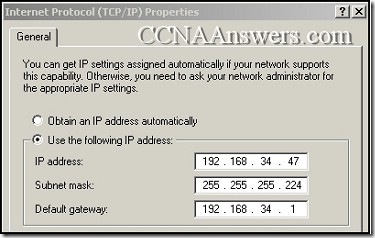
Refer to the exhibit. R1 is routing between networks 192.168.10.0/28 and 192.168.30.0/28. PC1 can ping R1 interface F0/1, but cannot ping PC3. What is causing this failure?
PC1 and PC3 are not in the same VLAN.
The PC3 network address configuration is incorrect.
The S1 interface F0/11 should be assigned to VLAN30.
The F0/0 and F0/1 interfaces on R1 must be configured as trunks.