CCNA Discovery 3 Final V4.0 Answers
1.
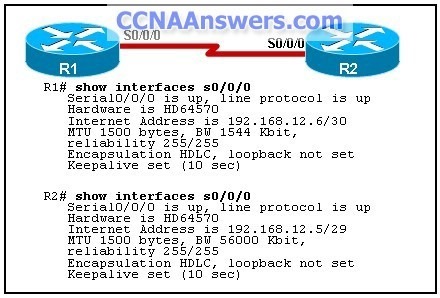
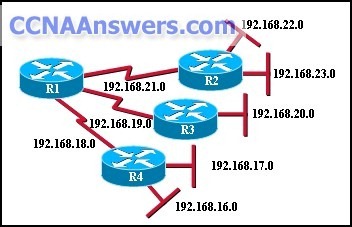
Refer to the exhibit. R1 and R2 are connected via serial interfaces. Both interfaces show that there is Layer 2 connectivity between them. The administrator verifies that CDP is operational; however, pings between the two interfaces are unsuccessful. What is the cause of this connectivity problem?
no set loopback
incorrect subnet mask on R2
incompatible bandwidth
incorrect IP address on R1
incompatible encapsulation
2. What are two benefits of using ACLs? (Choose two.)
They provide IP filtering.
They reduce the processing load on the router.
They simplify the configuration of inter-VLAN routing.
They prevent routing loops and facilitate convergence.
They identify traffic for multiple uses such as QoS and NAT.