CCNA 4 Practice Final Exam V4.0 Answers
1. What are two characteristics of DSL technology? (Choose two.)
Uploads typically offer larger transfer rates than downloads.
Service providers deploy DSL in the local loop of the telephone network.
DSL download rates are reduced by large volumes of POTS voice traffic.
Filters and splitters allow POTS and DSL traffic to share the same medium.
DSL is a shared medium that allows many users to share bandwidth available from the DSLAM.
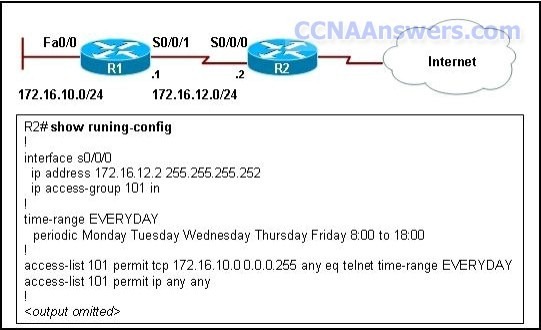
2.
Refer to the exhibit. What is the effect of the extended ACL when applied inbound on the S0/0/0 interface on R2?
All IP traffic will be permitted during the specified days and time range.
Both IP and Telnet traffic will be permitted during the specified days and time range.
Only Telnet traffic destined for 172.16.10.0/24 will be permitted during the specified days and time range.
Telnet traffic will be permitted only during the specified days and time range. All other network traffic will be permitted any time.