CCNA 3 Final Exam Answers 2012
1. A wireless client is attempting to establish a connection with a wireless access point. What process does the client use to discover the access points which are available to it?
probing
beaconing
association
authentication
2.
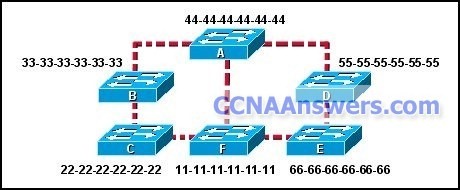
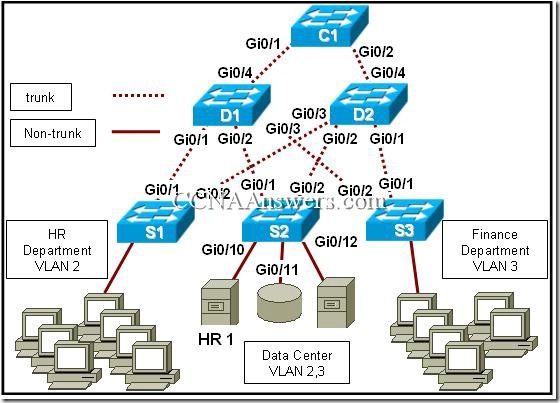
Refer to the exhibit. Each switch is shown with its MAC address. Which switch will be elected as the spanning-tree root bridge if the switches are configured with their default priority values?
switch A
switch B
switch C
switch D
switch E
switch F