CCNA 4 Final Exam V6.0 Answers
1. Refer to the exhibit. A network administrator is troubleshooting the OSPF network. The 10.10.0.0/16 network is not showing up in the routing table of Router1. What is the probable cause of this problem?
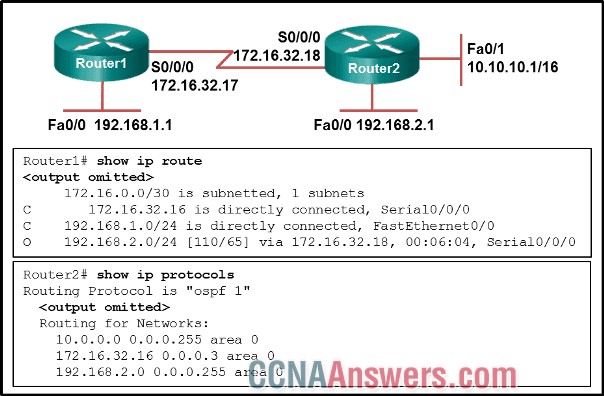
The serial interface on Router2 is down.
There is an incorrect wildcard mask statement for network 10.10.0.0/16 on Router2.
The OSPF process is configured incorrectly on Router1.
The OSPF process is not running on Router2.
2. What two protocols are supported on Cisco devices for AAA communications? (Choose two.)
RADIUS
HSRP
LLDP
VTP
TACACS+