CCNA Discovery 4 Chapter 7 V4.0 Answers
1.
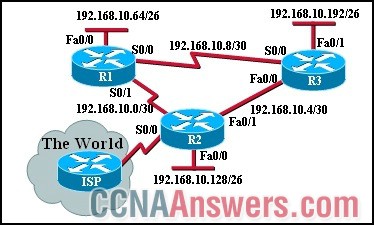
Refer to the exhibit. The users on the 192.168.10.192 network are not allowed Internet access. The network design calls for an extended ACL to be developed and tested. Where the ACL should be placed for the least effect on other network traffic?
• inbound on Fa0/0 of R3
• outbound on Fa0/0 of R3
• inbound on Fa0/1 of R3
• outbound on Fa0/1 of R3
• inbound on Fa0/1 of R2
• outbound on S0/0 of R2
2.
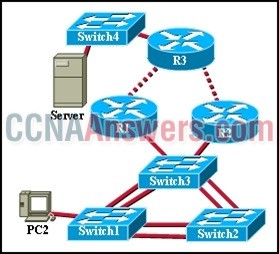
Refer to the exhibit. The redundant paths are of equal bandwidth and EIGRP is the routing protocol in use. Which statement describes the data flow from Server to PC2?
• EIGRP load balances across the R3 to R1 and R3 to R2 links.
• EIGRP load balances across the R1 to Switch3 and R2 to Switch3 paths.
• EIGRP load balances across the Switch1 to Switch3 and Switch1 to Switch2 paths.
• EIGRP does not load balance in this topology.
3.
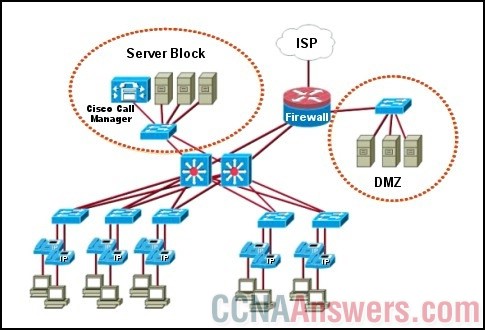
Refer to the exhibit. What two measures can be taken to address the areas of weakness circled in the network design? (Choose two.)
• Provide redundant connections to all end users.
• Add another core switch to increase redundancy.
• Add a switch in the server block connecting the server farm to each core switch.
• Add an additional switch to the DMZ and direct links from the new switch to the core switches.
• Provide a redundant firewall router connecting to a second ISP, the core switches, and the DMZ.
4. A network engineer has decided to pilot test a portion of a new network design rather than rely on a prototype for proof-of-concept. What are two advantages of pilot testing a design concept? (Choose two.)
• The test network experiences real-world network traffic.
• Users within the enterprise are not affected by the test.
• Network response can be tested in unplanned and unpredictable situations.
• Unlikely failure conditions can be conveniently tested.
• Network response can be tested in a highly controlled simulated environment.
5. When a switch port is recovering from a failure, which protocol allows the port to transition directly to the forwarding state?
• BGP
• HSRP
• RSTP
• VPN
• VTP
6.
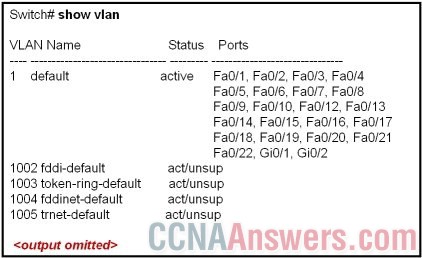
Refer to the exhibit. Why are interfaces Fa0/11, Fa0/23, and Fa0/24 not shown in this switch output?
• Interfaces Fa0/11, Fa0/23, and Fa0/24 are trunk ports.
• Interfaces Fa0/11, Fa0/23, and Fa0/24 are shut down.
• Interfaces Fa0/11, Fa0/23, and Fa0/24 are blocking.
• Interfaces Fa0/11, Fa0/23, and Fa0/24 failed diagnostics.
7.
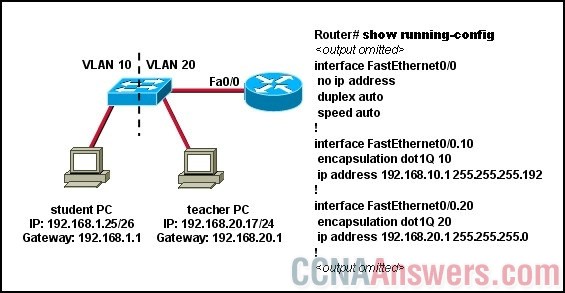
Refer to the exhibit. A network administrator has been given the task of creating a design for a temporary classroom building that is to be set up outside an overcrowded school. In testing the prototype, it is found that the student PC cannot ping the teacher PC. All the switch interfaces are active and connected properly, as is interface Fa0/0 of the router. Given that only the commands shown have been added to the router configuration, what is the source of the problem?
• The IP settings on the student PC are incorrect
• The default gateway on the teacher PC is misconfigured.
• The router Fa0/0 interface has not been configured as a VLAN trunk.
• The Fa0/0 physical interface has not been configured with an IP address and subnet mask.
• The administrator forgot to configure a routing protocol to allow the ping packets to reach the teacher PC subnet.
8. A network designer must provide a rationale to a customer for a design which will move an enterprise from a flat network topology to a hierarchical network topology. Which two features of the hierarchical design make it the better choice? (Choose two.)
• lower bandwidth requirements
• reduced cost for equipment and user training
• easier to provide redundant links to ensure higher availability
• less required equipment to provide the same performance levels
• ability to add access layer modules without affecting existing users
9.
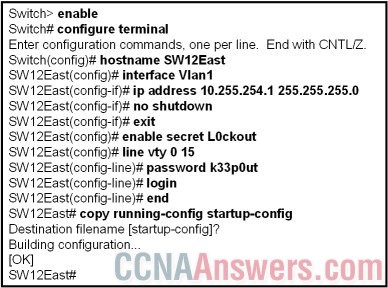
Refer to the exhibit. A network technician is performing an initial installation of a new switch in the east wing. The technician removes the switch from the box, makes the connections to the network, and adds the configuration shown. The technician notifies the network administrator that the switch has been installed. When the network administrator at the home office attempts to telnet to the switch from host 192.168.0.1, the connection fails. What action should the network technician take?
• Add an enable password to the switch.
• Add a default gateway to the switch configuration.
• Configure the switch with an IP access list to permit the host connection.
• Enable the physical interfaces of the switch with the no shutdown command.
10. For the multiple tests that are required to complete a LAN design test plan, which action should be taken as a component of every test?
• Verify physical and IP connectivity.
• Demonstrate multiple VLANs.
• Document the operation.
• Demonstrate routing of traffic between separate VLANs.
• Demonstrate 802.1q trunk link operation.
11. Why is it important to record baseline measurements of a prototype network?
• Test results show security weaknesses after the baseline tests are run.
• The baseline is the point at which the network is operating at its fullest potential.
• Baseline measurements define a point at which network traffic has exceeded the designed capabilities of the network.
• Test results are compared to the baseline to see how the test conditions increase processor use or decrease available bandwidth.
12.

Refer to the exhibit. After all the interfaces have stabilized, what is the spanning-tree state of all the enabled interfaces of SW11?
• discarding
• forwarding
• learning
• listening
13. Switch port Fa0/24 was previously configured as a trunk, but now it is to be used to connect a host to the network. How should the network administrator reconfigure switch port Fa0/24?
• Use the switchport mode access command from interface configuration mode.
• Enter the switchport nonegotiate command from interface configuration mode.
• Administratively shut down and re-enable the interface to return it to the default.
• Use the switchport access vlanvlan number command from interface configuration mode to remove the port from the trunk and add it to a specific VLAN.
14.
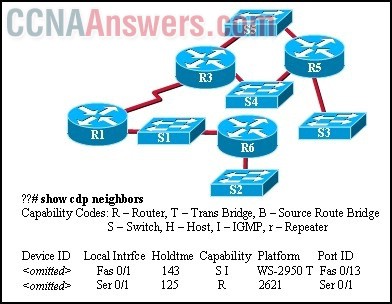
Refer to the exhibit. During prototype testing of the Cisco network shown, connectivity must be verified. Assuming all connections are working and CDP is enabled on all devices and interfaces, on which device was the command issued?
• R1
• S1
• R3
• S2
• R5
• S3
15. A network designer needs to determine if a proposed IP addressing scheme allows efficient route summarization and provides the appropriate amount of scalability to a design. What is useful for validating a proposed hierarchical IP addressing scheme?
• NBAR
• a pilot network
• a route summary
• a network simulator
• a physical topology map
16.
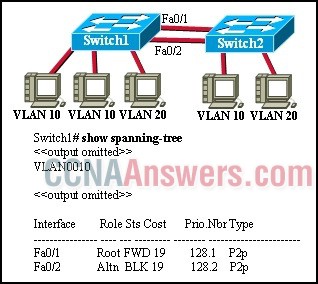
Refer to the exhibit. During prototyping, Layer 2 functionality is being tested. Based on the output shown, which two pieces of information can be determined? (Choose two.) Switch1 is the root bridge.
• Interface Fa0/2 on Switch1 has no role in the operation of spanning tree.
• Interface Fa0/2 on Switch1 is the alternate port used to reach the root bridge.
• Based on the entries in the "Role" column, it can be concluded that RSTP has been implemented.
• Interface Fa0/1 on Switch1 is the forwarding port selected for the entire spanning-tree topology.
17. When implementing RSTP, what is the designation for a port on a nonroot switch that blocks the port from forwarding?
• alternate
• backup
• designated
• root
18. Which is the next step in evaluating the performance of a network once the prototype is configured and basic connectivity is verified?
• Generate different traffic types to see the effects on performance.
• Start testing at Layer 2 by verifying link failure recovery.
• Create a network baseline.
• Trace the packet route through the network.
19.
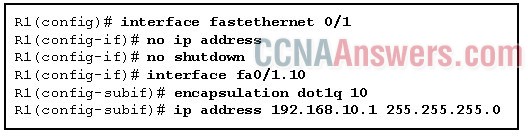
Refer to the exhibit. In the router command encapsulation dot1q 10, what does the number 10 represent?
• the metric that is used for a particular route
• the number that must match the Fast Ethernet subinterface number
• the priority number that is given to the device for the election process
• the identifier of the VLAN that is associated with the encapsulated subinterface
• the number that is used to program the router for unequal-cost path load balancing
20. How do designers decide which network functions need to be included in the prototype test?
• They select the functions that align with the business goals.
• They select the functions that occur at the network core.
• They select the functions that do not exist in the existing network.
• They select the functions from a list of generic network operations.
21. What OSI model Layer 2 security measure can a network engineer implement when prototyping network security?
• a firewall at the network edge
• port security at the access design layer
• port security at the distribution design layer
• IP access control lists at the access design layer
22. While preparing a network test plan document, a network designer records all initial and modified device configurations. Which section of the document typically contains this information?
• Appendix
• Test Procedures
• Test Description
• Actual Results and Conclusions
• Anticipated Results and Success Criteria
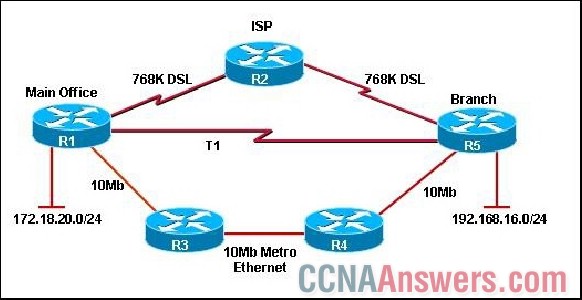
23.
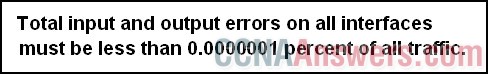
Refer to the exhibit. A network designer creates a test plan that includes the specification shown. In which section of the test plan would this specification be found?
• Test Description
• Test Procedures
• Design and Topology Diagram
• Actual Results and Conclusions
• Anticipated Results and Success Criteria
24. What Rapid Spanning Tree Protocol (RSTP) state is given to the forwarding port elected for every switched Ethernet LAN segment?
• root
• backup
• alternate
• designated


Leave a Reply