CCNA Discovery 2 Final V4.1 Answers
1.
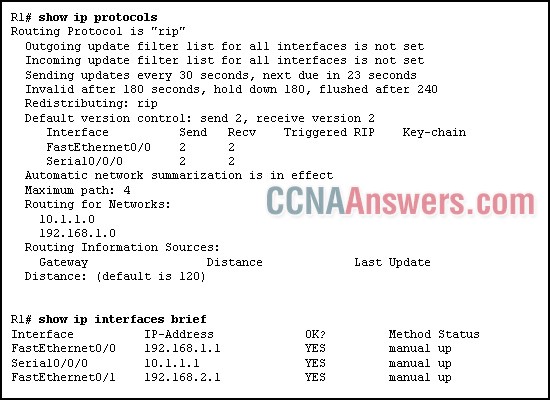
Refer to the exhibit. Which statement is true based on the exhibited information?
The router is using a link-state routing protocol.
The router will get routing updates on the FastEthernet0/0 interface.
The router will not forward routing updates from the Serial0/0/0 interface.
The network for Fa0/1 will be included in the routing updates that are sent from this router.
2. Which two tasks should be part of a disaster recovery plan? (Choose two.)
backing up data
installing intrusion detection systems
protecting information from malicious attack
ensuring that traffic from clients to servers is encrypted
identifying offsite locations where services and operations can be moved
3.
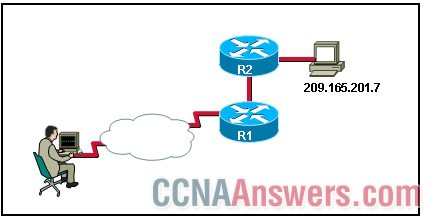
Refer to the exhibit. A NOC technician at an ISP enters the command c:\ping 209.165.201.7. What are two reasons to use this command? (Choose two.)
map the path to 209.165.201.7
test reachability to 209.165.201.7
locate connectivity problems along the route to 209.165.201.7
identify ISPs that interconnect the NOC and remote host with IP 209.165.201.7
measure the time that packets take to reach 209.165.201.7 and return to the technician's workstation
4. Which protocol allows secure in-band management so that a network administrator can monitor and configure network devices without fear of any passwords being compromised?
SSH
HTTP
SNMP
Telnet
5. Which statement is correct about passive data connections in the FTP protocol?
The server initiates the data transfer connection.
The server forwards its IP address and a random port number to the FTP client through the control stream.
The firewalls do not permit passive data connections to hosts that are located within the network.
The client forwards data to port 21 of the server.
6. In the URL http://dev.cisco.com/wwwdocs/procedures.htm, what is identified by wwwdocs?
the server name where the resource is located
the protocol that is used for the resource request
the domain name of the server that is being accessed
the folder where the requested resource is stored
7. A network technician begins troubleshooting by checking the status of the light on the network interface card on the web server. Which troubleshooting method is the technician using?
top-down
bottom-up
divide-and-conquer
from hardware to software
8.
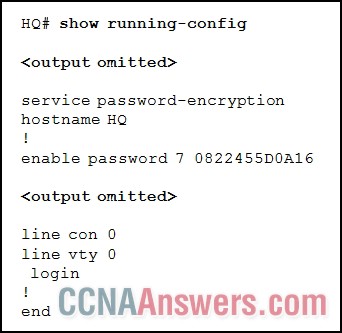
Refer to the exhibit. What is the possible reason that a technician is unable to telnet into the HQ router and make configuration changes?
A password is required for vty 0.
A password for line con 0 is required.
All five virtual interfaces must be configured before Telnet is possible.
The service password-encryption command is preventing Telnet access.
9. An administrator wishes to protect a router by encrypting the console access password noaccess. Which command should be used?
Router(config)# enable secret noaccess
Router(config)# enable password noaccess
Router(config-line)# password noaccess
Router(config)# service password-encryption
10. Which type of cable may be used for backbone cabling between data centers that are located on different floors and that are separated by a distance of 1640 feet (500 meters)?
STP
UTP
coaxial
fiber-optic
11.
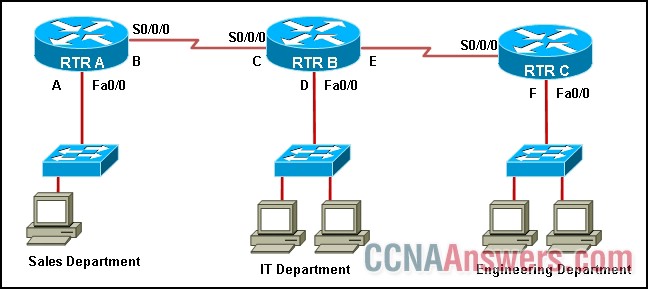
Refer to the exhibit. Hosts that belong to the IT department use 10.10.55.33/27 as a default gateway. Where can this IP address be located in the network?
A
B
C
D
12. Which router component can be configured with parameters that apply to all Telnet sessions to the router?
AUX port
VTY ports
console port
FastEthernet interface
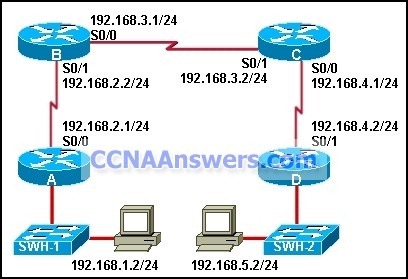
13.
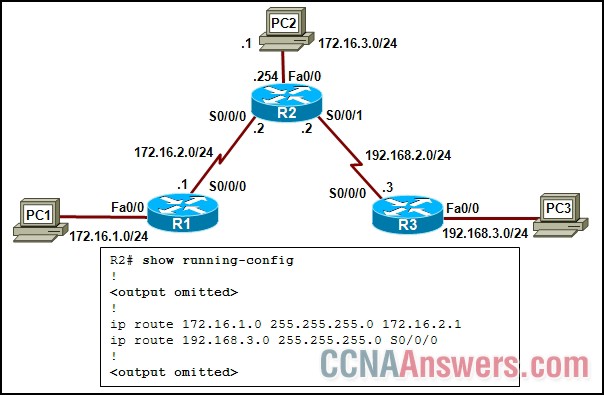
Refer to the exhibit. Static routes have been configured on all routers in the network. PC2 can communicate with PC1 but not with PC3. What should be done to remedy the problem?
Reconfigure the first static route with the exit interface S0/0/0.
Reconfigure the second static route with the exit interface S0/0/1.
Reconfigure the first static route with the next hop address 172.16.3.1.
Reconfigure the second static route with the next hop address 172.16.3.1.
14. In an IPv4 environment, what information is used by the router to forward data packets from one interface of a router to another?
destination network address
source network address
source MAC address
well known port destination address
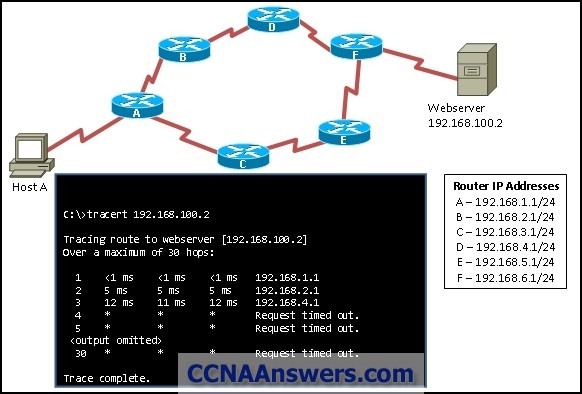
15.
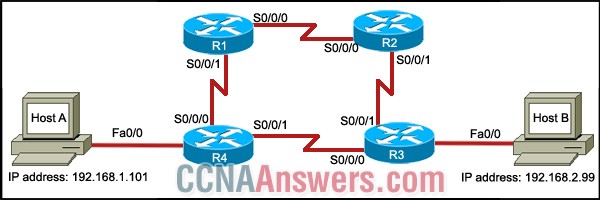
Refer to the exhibit. A network technician issues the tracert 192.168.2.99 command successfully on host A. What are two consequences of running this command? (Choose two.)
The traceroute packet is broadcast to the network.
The command output will display the IP address of both the inbound and outbound router interfaces that the packet passes through.
The command output will display all routers through which the packet has passed.
All successful hops between host A and host B will reply to the echo request with a proxy ICMP response.
The command will calculate the time between when the packet is sent and when a reply is received from a router.
16. For the assignment of permissions to files and folders, what does the "principle of least privilege" imply?
No user has more privileges than any other user.
Permissions to files are given based on seniority.
Users only have access to resources that are necessary for their jobs.
Users should be given no access to computer resources until they ask.
17. What is a feature of PAT?
It maps IP addresses to URLs.
It displays private IP addresses to public networks.
It sends acknowledgments of received packets.
It allows multiple hosts on a single LAN to share globally unique IP addresses.
18. Which type of address is 192.168.17.111/28?
host address
network address
broadcast address
multicast address
19. For an HTTP server, what purpose does a URL server?
ensures that routing tables are up to date
translates domain names into IP addresses
determines which services are available on a server
identifies the protocol and path to resources on a server
20. Which two processes enable a router to determine paths to destination networks? (Choose two.)
inspection of the source IP address in data packets
ARP requests from connected routers
manual configuration of routes
updates from other routers
DHCP information broadcasts
updates from the SMTP management information base
21.
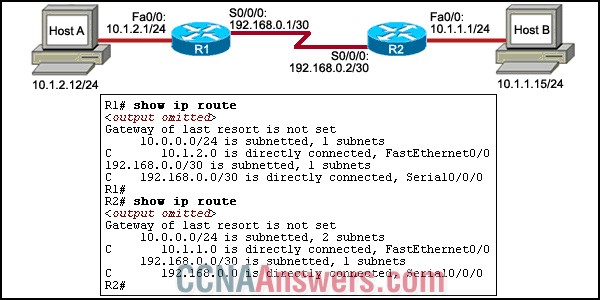
Refer to the exhibit. Host A is unable to ping host B. What can be done to solve this problem? (Choose two.)
Configure a default route on R1 with the use of exit interface Fa0/0.
Configure a default route on R2 by using the exit interface Fa0/0.
Configure a static route on R1 with 192.168.0.1/24 as the next hop address.
Configure a static route for network 10.1.2.0/24 on R2 and use exit interface S0/0/0.
Configure a static route for network 10.1.1.0/24 on R1 with the next hop address as the IP address of the serial interface of R2.
22. A user is able to ping IP addresses but is unable to ping hosts by domain name. What should be checked at the workstation of the user?
the device driver configuration of NIC
the LED status of the NIC
the DNS configuration
the firewall settings
23.

Refer to the exhibit. Which type of link is supported by this interface module?
LAN
WAN
WLAN
VLAN
24. As a host prepares a message for communication, a header and trailer are added and the data is placed on the medium for transmission to the next directly connected device. At which two layers of the OSI model do these activities occur? (Choose two.)
session
network
physical
transport
data link
application
presentation
25. What is the primary function of the NOC at a large ISP?
installing equipment at a customer site
setting up customer accounts and passwords
monitoring and testing customer network connections
entering customer requirements in an order-tracking database
26. A hacker attempts to reach confidential information that is stored on a server inside the corporate network. A network security solution inspects the entire packet, determines that it is a threat, and blocks the packet from entering the inside network. Which security measure protected the network?
an IDS
an IPS
a host-based firewall
Anti-X software
27. If the NVRAM on a router were to fail, which router resource would be lost?
IOS software image
ROMmon software
running configuration
startup configuration
28. A company is developing an Internet store for its website. Which protocol should be used to transfer credit card information from customers to the company web server?
FTPS
HTTP
HTTPS
WEP2
TFTP
29. Which statement correctly describes the function of AAA?
It prevents unauthorized access to a network.
It filters traffic based on destination IP and port number.
It enables users to send information to a daemon that is running on a management station.
It encrypts data to provide network security.
30. Different hosts connect to the same switch port at different times. If the switch port is configured with dynamic port security, how does it process the MAC addresses?
The addresses are manually assigned with the use of the switchport command.
The addresses are dynamically learned and stored in the address table.
The addresses are dynamically configured and saved in the running configuration.
The addresses are stored in the address table and added to the running configuration.
31. Which service team in an ISP is responsible for determining if the new customer has hardware that will support the new WAN connection and if new WAN circuits need to be installed?
customer service
onsite installation
planning and provisioning
network operations center
32. Which type of WAN connection uses packet-switched connections?
T1
E1
ISDN
Frame Relay
33. When customers use credit cards to make purchases at a small business, a modem is heard dialing a telephone number to transfer the transaction data to the central office. What type of WAN serial connection is in use?
leased line
packet switched
circuit switched
point-to-point
34.
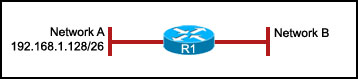
Refer to the exhibit. The network administrator must set up a network with two subnets. In network A, the network administrator selects the network address 192.168.1.128/26. Which address combination should the administrator select in network B to accommodate the same number of hosts as in network A?
192.168.1.32 255.255.255.128
192.168.1.0 255.255.255.224
192.168.1.64 255.255.255.192
192.168.1.192 255.255.255.128
35.
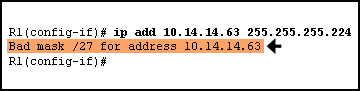
Refer to the exhibit. While configuring the serial interface of a router, the network administrator sees the highlighted error message. What is the reason for this?
The serial interface is administratively down.
The serial interface is already configured with an IP address.
The network administrator has attempted to configure the serialinterface with a broadcast address.
The same IP address has been configured on another interface.
36. Which routing protocol facilitates the exchange of routing information between different autonomous systems?
OSPF
EIGRP
RIP
BGP
37. Which mode does a router enter when no configuration file is located in NVRAM?
ROMMON
setup
global configuration
privileged exec
38.

Refer to the exhibit. What does the highlighted value 120 represent?
the number of hops between the router and network 10.0.5.0
the administrative distance of the routing protocol
the UDP port number that is used for forwarding traffic
the bandwidth that is allocated to the serial interface
39. Which cable type is used to interconnect the FastEthernet interfaces of two routers?
straight-through
Crossover
console
rollover
40. What is the effect of issuing the banner login #Unauthorized login prohibited# command on a router?
It will display the message "Unauthorized login prohibited" before the router prompts for a user name.
It replaces the banner motd command.
It causes the router to prompt for login credentials for any user who is attempting to connect to the router.
It causes the message "Unauthorized access prohibited" to display when a HyperTerminal connection is idle.
41.
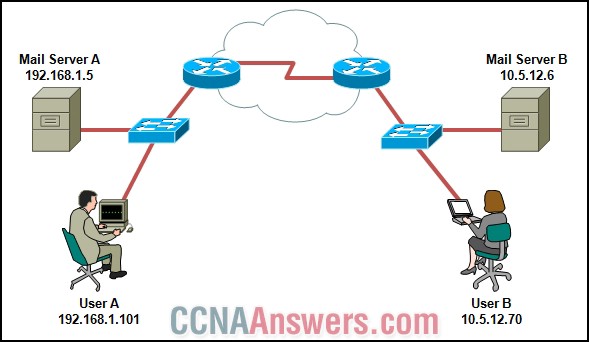
Refer to the exhibit. User A wants to send an e-mail to user B. To which IP address and TCP port will the e-mail application that is used by user A send the message?
10.5.12.6 port 25
10.5.12.6 port 110
10.5.12.70 port 25
10.5.12.70 port 110
192.168.1.5 port 25
192.168.1.5 port 110
42. Which networking service is used to provide name to IP address mapping?
DNS
FTP
NAT
DHCP
43. What is the purpose of the routing process?
to encapsulate data that is used to communicate across a network
to select the paths that are used to direct traffic to destination networks
to convert a URL name into an IP address
to provide secure Internet file transfer
to forward traffic on the basis of MAC addresses
44. What can be gained by using a caching-only DNS server?
The DNS server will use more WAN bandwidth.
The DNS server will only answer recursive queries.
The DNS server will be authoritative for only one zone.
The DNS server will resolve most queries more quickly.
45. Which address does a switch use for implementing port security?
the source IP address
the source MAC address
the destination IP address
the destination MAC address
46. In the relationship between an ISP and a customer, what is the purpose of an SLA?
It shows bandwidth utilization over time.
It documents expectations and obligations of both parties.
It helps technicians locate sources of service interruptions.
It provides performance baselines for network troubleshooting.
47.
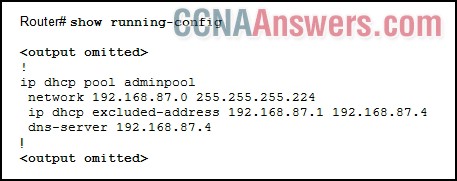
Refer to the exhibit. A PC has an IP address of 192.168.87.30 but is unable to contact a web server on the Internet. A network administrator is troubleshooting the DHCP configuration on a Cisco 1841 router. What is the possible error?
The IP address of the PC is outside the network range.
A domain name is required in the DHCP configuration.
The DHCP service has not been activated.
The default-router command needs to be included in the DHCP configuration.
The DHCP pool has not been applied to an active interface.
48. A user reports being able to access the Internet but not being able to download e-mail from the mail server at the ISP. What should the user check on the user workstation?
the POP3 and SMTP server settings in the e-mail application
the patch cable connections at the back of the workstation and at the wall plate
the DHCP settings in the operating system
the IP address, mask, and default gateway values
the NIC drivers
49. In a structured cable system, what is the purpose of horizontal cabling?
It connects an IDF to an IDF.
It connects an IDF to the MDF.
It connects wall jacks to an IDF.
It connects wall jacks to user workstations.
50.
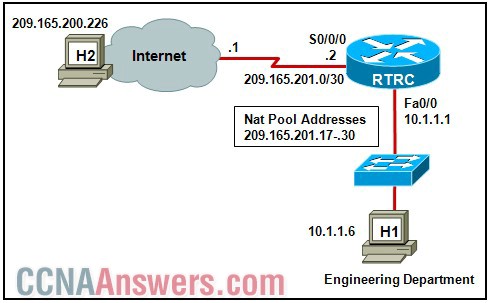
Refer to the exhibit. Host H1 is sending a datagram to host H2 across the Internet. NAT will be configured on RTRC. Which address is considered the inside local address?
10.1.1.1
10.1.1.6
209.165.201.2
209.165.201.17
209.165.200.226



Leave a Reply