CCNA 3 Chapter 7 V4.0 Answers
1. Which two statements concerning network security are accurate? (Choose two.)
802.11i uses 3DES for encryption.
Open authentication uses no client or AP verification.
The 802.11i protocol is functionally identical to WPA.
802.11i incorporates a RADIUS server for enterprise authentication.
A wireless client first associates with an AP and then authenticates for network access.
2. Which installation method will allow connectivity for a new wireless network?
set up WEP on the access point only
set up open access on both the access point and each device connected to it
set up full encryption on the access point while leaving each device connected to the network open
set up full encryption on each device of the WLAN while leaving the access point settings open
3. Which function is provided by a wireless access point?
dynamically assigns an IP address to the host
provides local DHCP services
converts data from 802.11 to 802.3 frame encapsulation
provides a gateway for connecting to other networks
4. What procedure can prevent man-in-the-middle attacks?
Force all devices on a WLAN to authenticate and monitor for any unknown devices.
Enable access points to send an SSID to each device wanting to use the network.
Configure MAC filtering on all authorized access points.
Disable SSID broadcasts.
5. What does a wireless access point use to allow WLAN clients to learn which networks are available in a given area?
association response
beacon
key
probe request
6. What wireless security feature allows a network administrator to configure an access point with wireless NIC unique identifiers so that only these NICs can connect to the wireless network?
authentication
SSID broadcasting
MAC address filtering
EAP (Extensible Authentication Protocol)
Radius (Remote Authentication Dial-In User Service)
7. Wireless users on a network complain about poor performance within a small area of a room. Moving away from this area in any direction improves performance dramatically. What is the first step in designing a solution to this problem?
This might be RF channel overlap, so the technician should verify the channels in use on each wireless access point and change to non-overlapping channels.
The RF power settings might be set too low on the wireless access points servicing the room. Increase the RF output power on all wireless access points.
Install a new wireless access point in this center area to provide coverage.
Verify that the wireless access points have sufficient in-line power and connectivity to the wired network.
8. Which two statements characterize wireless network security? (Choose two.)
A rogue access point represents a security risk for the local network.
Wireless networks offer the same security features as wired networks.
Using encryption prevents unauthorized clients from associating with an access point.
An attacker needs physical access to at least one network device to launch an attack.
With SSID broadcast disabled, an attacker must sniff the SSID before being able to connect.
9. Which network design process identifies where to place access points?
site survey
risk assessment
scalability design
network protocol analysis
10.
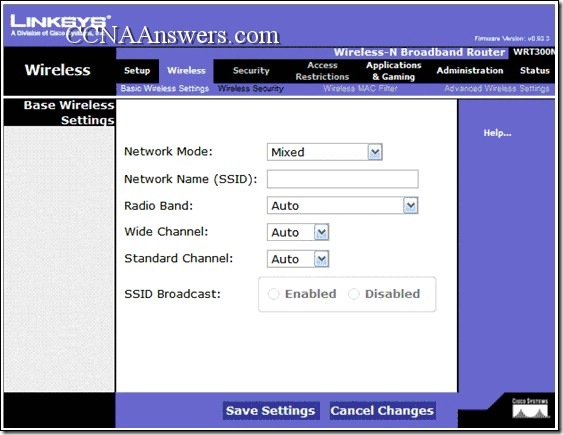
Refer to the exhibit. When configuring the wireless access point, which setting does the network administrator use to configure the unique identifier that client devices use to distinguish this wireless network from others?
Network Mode
Network Name (SSID)
Radio Band
Wide Channel
Standard Channel
11. Which two conditions have favored adoption of 802.11g over 802.11a? (Choose two.)
802.11a suffers from a shorter range than 802.11g.
The 2.4 GHz frequency band is not as crowded as the 5 GHz band.
802.11a is more susceptible to RF interference from common commercial items.
802.11a uses a more expensive modulation technique than 802.11g.
802.11g is backward compatible with 802.11b, but 802.11a is not.
12. What occurs when a rogue access point is added to a WLAN?
Authorized access points can transmit excess traffic to rogue access points to help alleviate congestion.
Unauthorized users can gain access to internal servers, thus causing a security hole.
All traffic that uses the same channel as the rogue access point will be encrypted.
All traffic that uses the same channel as the rogue access point will be required to authenticate.
13. In a WLAN network, why should wireless access points be implemented with each access point using a different channel?
to keep users segregated on separate subnets
to control the amount of bandwidth that is utilized
to keep signals from interfering with each other
to keep traffic secure
14. Which two statements are true regarding wireless security? (Choose two.)
MAC address filtering prevents the contents of wireless frames from being viewable.
Providing a wireless client with the network key allows an available network to be visible.
Disabling an access point from broadcasting the SSID prevents the access point from being discovered.
Default SSIDs on specific manufacturer APs are generally known and may permit hostile wireless connections.
Manually adding a network and setting the known SSID on a wireless client makes the network visible even if the SSID is not being broadcast.
15. Why is security so important in wireless networks?
Wireless networks are typically slower than wired networks.
Televisions and other devices can interfere with wireless signals.
Wireless networks broadcast data over a medium that allows easy access.
Environmental factors such as thunderstorms can affect wireless networks.
16. Which wireless technology standard provides the most compatibility with older wireless standards, but has greater performance?
802.11a
802.11b
802.11g
802.11n
17. Which three devices do many wireless routers incorporate? (Choose three.)
gateway for connecting to other network infrastructures
built-in Ethernet switch
network management station
VTP server
wireless access point
VPN concentrator
18. What will a wireless client transmit to discover the available WLAN networks?
beacon
password
probe request
association request
19. Which major problem does CSMA/CA overcome in wireless networks?
bandwidth saturation
privacy concerns
media contention
device interoperability
20. Which access method does a wireless access point use to allow for multiple user connectivity and distributed access?
CSMA/CD
token passing
CSMA/CA
polling
21. What purpose does authentication serve in a WLAN?
converts clear text data before transmission
indicates which channel the data should flow on
determines that the correct host is utilizing the network
allows the host to choose which channel to use



Leave a Reply