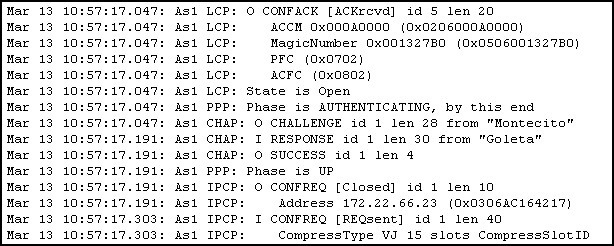
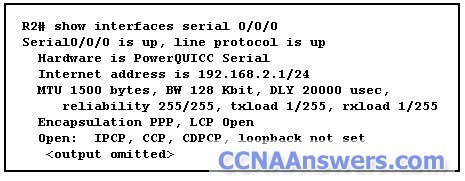
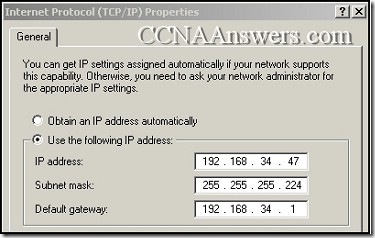
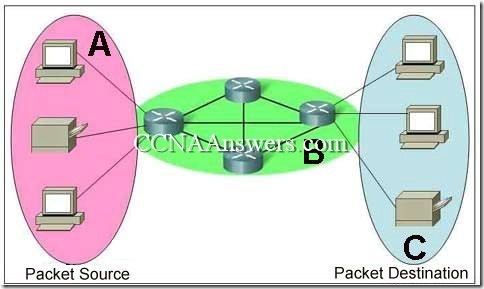
CCNA Discovery 4 Chapter 6 V4.0 Answers
1.
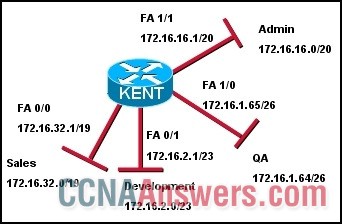
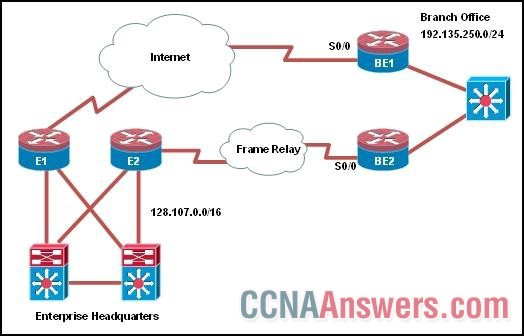
Refer to the exhibit. What are the broadcast addresses for each subnet?
• Admin – 172.16.31.0
QA – 172.16.1.127
Development – 172.16.2.255
Sales – 172.16.32.255
• Admin – 172.16.31.0
Development – 172.16.2.255
QA – 172.16.1.255
Sales – 172.16.63.255
• Admin – 172.16.31.255
Development – 172.16.3.255
QA – 172.16.1.127
Sales – 172.16.63.255
• Admin – 172.16.31.0
QA – 172.16.1.255
Development – 172.16.2.255
Sales – 172.16.32.255
2. How many bits make up an IPv6 address?
• 32
• 48
• 64
• 128
• 132