CCNA 3 Chapter 1 V6.0 Answers
1. A network administrator is planning redundant devices and cabling in a switched network to support high availability. Which benefit will implementing the Spanning Tree Protocol provide to this design?
Faster convergence is available for advanced routing protocols.
Multiple physical interfaces can be combined into a single EtherChannel interface.
Redundant paths can be available without causing logical Layer 2 loops.
Network access can be expanded to support both wired and wireless devices.
2. Refer to the exhibit. Which devices exist in the failure domain when switch S3 loses power?
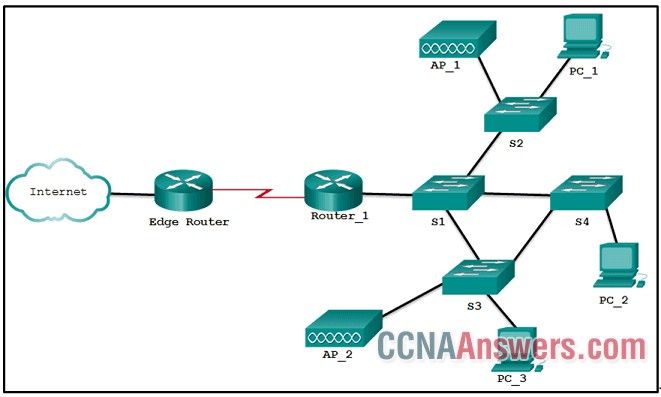
PC_3 and AP_2
PC_3 and PC_2
S4 and PC_2
AP_2 and AP_1
S1 and S4